9.2.1. IPsec LAN to LAN with Pre-shared Keys
1. Create a Pre-shared Key object.
2. Optionally create a new IKE Algorithms object and/or an IPsec Algorithms object if the
default algorithm proposal lists do not provide a set of algorithms that are acceptable to the
tunnel remote end point. This will depend on the capabilities of the device at the other end of
the VPN tunnel.
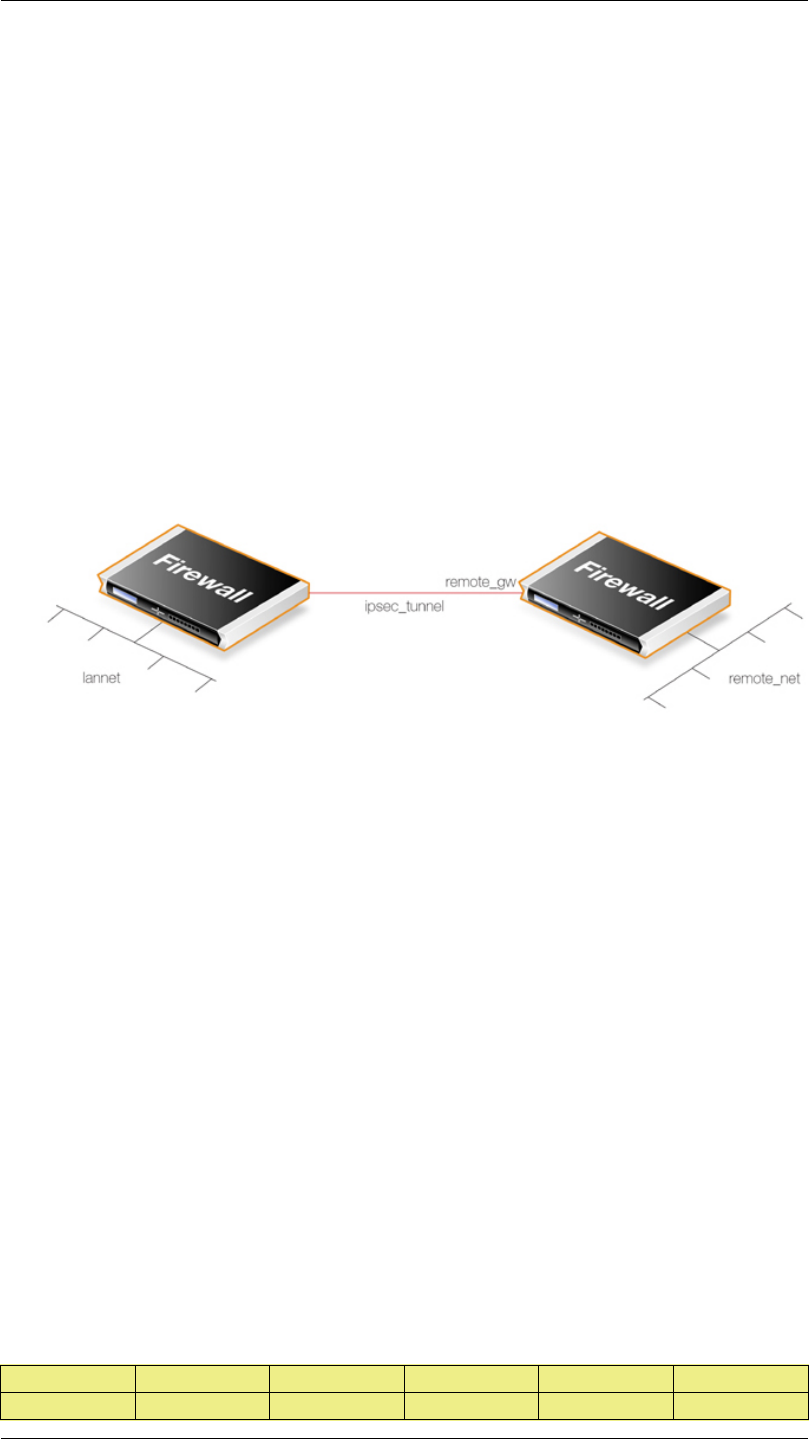
3. In the Address Book create IP objects for:
• The remote VPN gateway which is the IP address of the network device at the other end of
the tunnel (let's call this object remote_gw).
• The remote network which lies behind the remote VPN gateway (let's call this object
remote_net).
• The local network behind the NetDefend Firewall which will communicate across the
tunnel. Here we will assume that this is the predefined address lannet and this network is
attached to the NetDefendOS lan interface.
4. Create an IPsec Tunnel object (let's call this object ipsec_tunnel). Specify the following tunnel
parameters:
• Set Local Network to lannet.
• Set Remote Network to remote_net.
• Set Remote Endpoint to remote_gw.
• Set Encapsulation mode to Tunnel.
• Choose the IKE and IPsec algorithm proposal lists to be used.
• For Authentication select the Pre-shared Key object defined in step (1) above.
The IPsec Tunnel object can be treated exactly like any NetDefendOS Interface object in later
steps.
5. Set up two IP rules in the IP rule set for the tunnel:
• An Allow rule for outbound traffic that has the previously defined ipsec_tunnel object as
the Destination Interface. The rule's Destination Network is the remote network
remote_net.
• An Allow rule for inbound traffic that has the previously defined ipsec_tunnel object as the
Source Interface. The Source Network is remote_net.
Action Src Interface Src Network Dest Interface Dest Network Service
Allow lan lannet ipsec_tunnel remote_net All
9.2.1. IPsec LAN to LAN with
Pre-shared Keys
Chapter 9. VPN
382


















