Chapter 4. Tuning the operating system 103
Draft Document for Review May 4, 2007 11:35 am 4285ch04.fm
policy model that overcomes the limitations of the standard discretionary access model
employed by Linux. SELinux enforces security on user and process levels; hence a security
flaw of any given process affects only the resources allocated to this process and not the
entire system. SELinux works similar to a virtual machine. For example, if a malicious attacker
uses a root exploit within Apache, only the resources allocated to the Apache daemon could
be compromised.
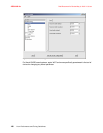
Figure 4-4 Schematic overview of SELinux
However, enforcing such a policy-based security model comes at a price. Every access from
a user or process to a system resource such as an I/O device must be controlled by SELinux.
The process of checking permissions can cause overhead of up to 10%. SELinux is of great
value to any edge server such as a firewall or a Web server, but the added level of security on
a back-end database server may not justify the loss in performance.
Generally the easiest way to disable SELinux is to not install it in the first place. But often
systems have been installed using default parameters, unaware that SELinux affects
performance. To disable SELinux after an installation, append the entry selinux=0 to the line
containing the running kernel in the GRUB boot loader (Example 4-3 on page 103).
Example 4-3 Sample grub.conf file with disabled SELinux
default=0
splashimage=(hd0,0)/grub/splash.xpm.gz
hiddenmenu
title Red Hat Enterprise Linux AS (2.6.9-5.ELsmp)
root (hd0,0)
kernel /vmlinuz-2.6.9-5.ELsmp ro root=LABEL=/ selinux=0
initrd /initrd-2.6.9-5.ELsmp.img
Another way of disabling SELinux is via the SELinux configuration file stored under
/etc/selinux/config. Disabling SELinux from within that file looks as shown in the next
example Example 4-4 on page 103.
Example 4-4 Disabling SELinux via the config file
# This file controls the state of SELinux on the system.
# SELINUX= can take one of these three values:
# enforcing - SELinux security policy is enforced.
# permissive - SELinux prints warnings instead of enforcing.
SELinux Kernel
SECURITY
POLICY
SECURITY
ENFORCEMENT
MODULE
Process
User
SYSTEM
RESOURCES
Request
Access
Grant
Access
Grant/Deny Access
Based on Policy