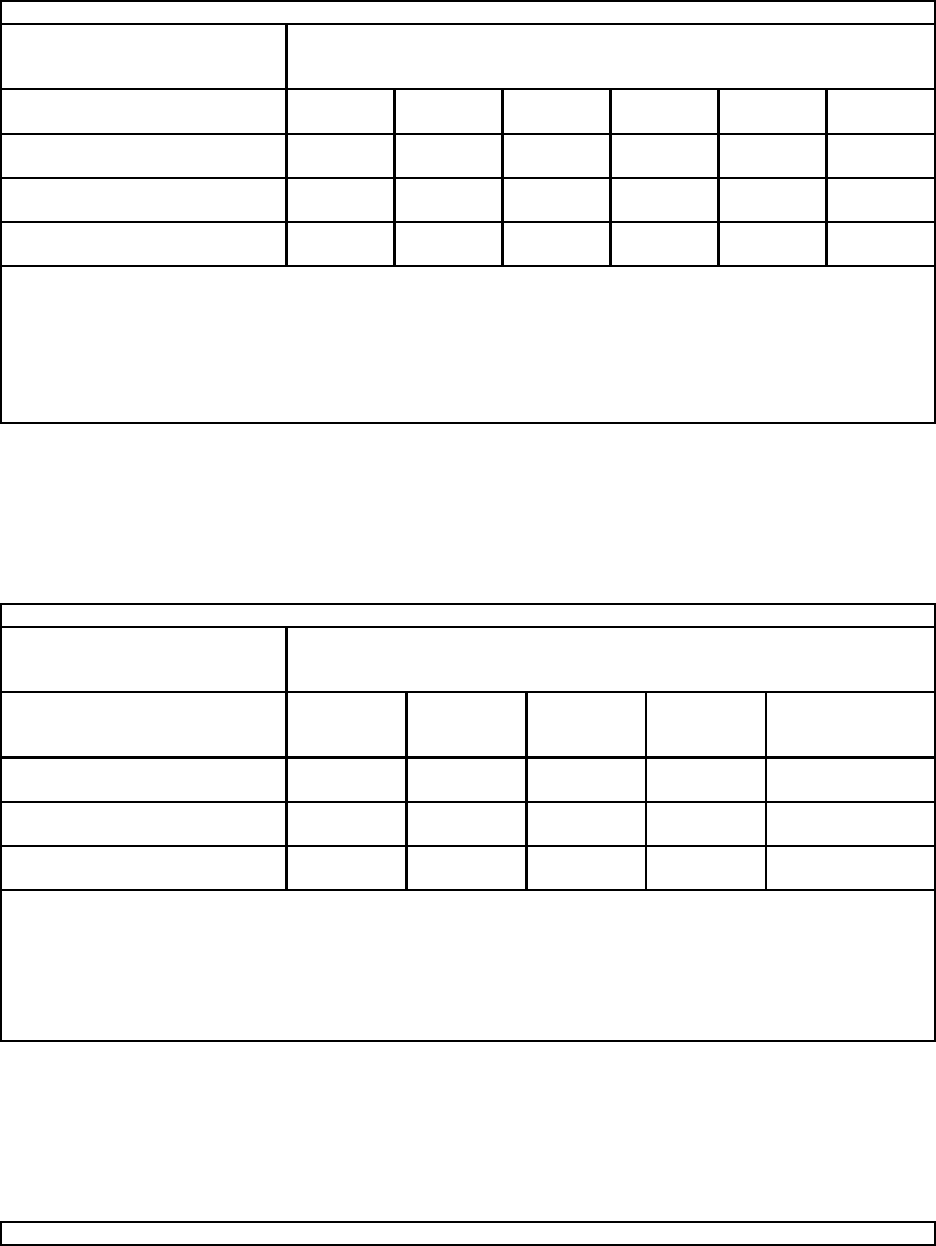
Notes:
y Capacity metrics are provided for nonsecure and each variation of security policy
y The table data reflects System i as a server (not a client)
y This is only a rough indicator for capacity planning. Actual results may differ significantly.
y Each SSL connections was established with a 1024 bit RSA handshake.
y x, y and z are scaling constants, one for each NetPerf scenario.
73.715.013.09.08.61.0 z
Large Transfer
(Stream) 16K Bytes
51.79.18.05.24.71.0 y
Asym. Connect/Request/Response
(ACRR) 8K Bytes
5.82.52.42.22.11.0 x
Request/Response
(RR) 128 Byte
TDES /
SHA-1
AES256 /
SHA-1
AES128 /
SHA-1
RC4 /
SHA-1
RC4 /
MD5
Nonsecure
TCP/IP
Transaction Type:
SSL Relative Performance
(scaled to Nonsecure baseline)
Table 5.7
VPN
Although the term Virtual Private Networks (VPN) didn’t start until early 1997, the concepts behind VPN
started around the same time as the birth of the Internet. VPN creates a secure tunnel to communicate
from one point to another using an unsecured network as media. Table 5.8 provides some rough capacity
planning information for VPN communication, when using 1 Gigabit Ethernet.
Notes:
y Capacity metrics are provided for nonsecure and each variation of security policy
y The table data reflects System i as a server (not a client)
y VPN measurements used transport mode, TDES, AES128 or RC4 with 128-bit key symmetric cipher and MD5 message
digest with RSA public/private keys. VPN antireplay was disabled.
y This is only a rough indicator for capacity planning. Actual results may differ significantly.
5.425.631.044.0478.4
Large Transfer
(Stream) 16K Bytes
9.132.737.749.9249.7
Asym. Connect/Request/Response
(ACRR) 8K Bytes
148.4307.71322.9428.51167.0
Request/Response
(RR) 128 Byte
ESP with TDES /
SHA-1
ESP with
AES128 /
SHA-1
ESP with
RC4 / MD5
AH with
MD5
Nonsecure
TCP/IP
Transaction Type:
VPN Performance
(transactions per second per server CPU)
Table 5.8
This table also shows a range of encryption methods to give you an insight on the performance between
less secure but faster, or more secure but slower methods, all compared to unsecured TCP/IP.
Table 5.9 below illustrates relative CPU consumption for VPN instead of potential capacity. Essentially,
this is a normalized inverse of the CPU capacity data from Table 5.6. It gives another view of the impact
of choosing one security policy over another for various NetPerf scenarios.
Table 5.9
IBM i 6.1 Performance Capabilities Reference - January/April/October 2008
© Copyright IBM Corp. 2008 Chapter 5 - Communications Performance 71


















