Radius operation
25
the AP. If a WEP key has been stored in the
Radius database for this station, it uses the
Blowfish algorithm to encrypt the WEP key and
includes this as a Vendor-Specific Radius
attribute. Otherwise, no Vendor-Specific
attribute is included.
The WEP key is transmitted as a 32-character
hexadecimal ASCII string derived as follows:
• Copy the n-byte WEP key to a 16-byte
buffer.
• Fill the remainder of the buffer with 0x00.
• Encrypt the 16-byte buffer using Blowfish
with the
shared secret as the key.
• Encode the 16-byte buffer as a 32-character
hexadecimal string.
The WEPkeygen utility provided with the AP
can be used to generate the encrypted keys. The
data can be entered as normal, and saved to a
file instead of being sent to the AP. This is a
simple text file, and the encrypted key values
can be copied across to the Radius database.
The 32-character string representing the
encrypted key is sent to the AP as a vendor-
specific attribute (see RFC2138 section 5.26)
with the vendor ID set to the Nokia value (94).
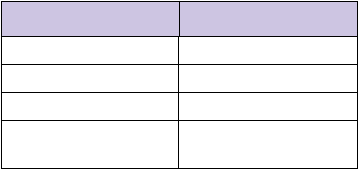
This is shown below.
Field Octets
Type (26) 1
Length 1
Vendor ID (94) 4
WEP key attribute
(see following tables)
34 or 36


















