Configuring the Switch
3-30
Configuring the Secure Shell
The Berkley-standard includes remote access tools originally designed for Unix
systems. Some of these tools have also been implemented for Microsoft Windows
and other environments. These tools, including commands such as, rsh (remote
shell), and rexec (remote execute), are not secure from hostile attacks.
The Secure Shell (SSH) includes server/client applications intended as a secure
replacement for the older Berkley remote access tools. SSH provides remote
management access via encrypted paths between the switch and SSH-enabled
management station clients. The commands described in this section include
commands used to configure the SSH server. However, you also need to install a
SSH client on the management station when using this protocol to configure the
switch. When the client contacts the switch via the SSH protocol, the switch
generates a public-key that the client uses along with a local user name and
password for access authentication.
Note: The switch supports only SSH Version 1.5.
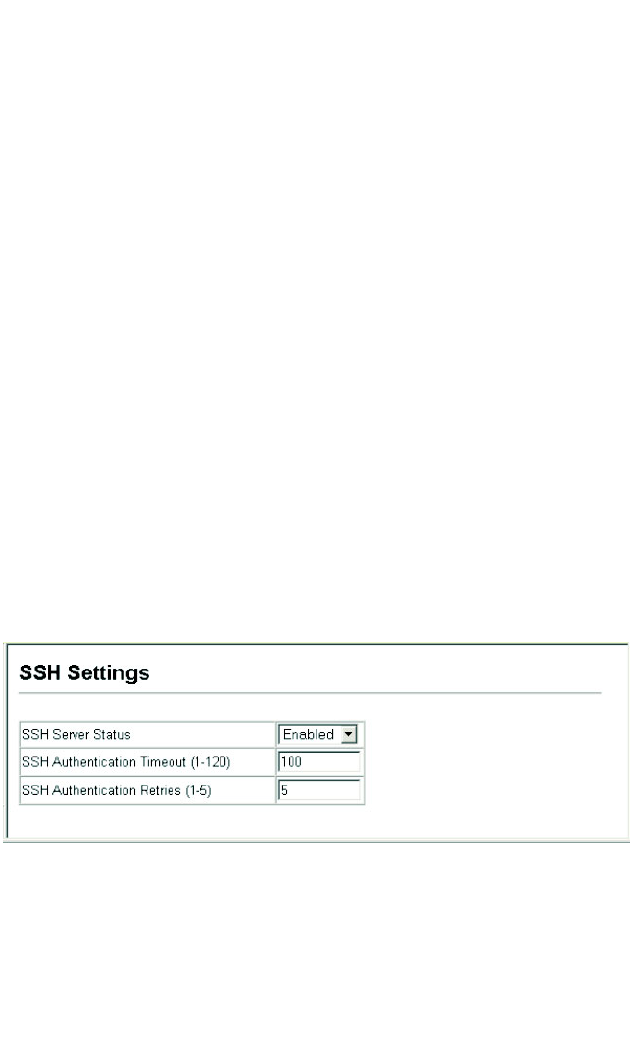
Command Attributes
• SSH Server Status – Allows you to enable/disable the SSH server feature on
the switch. (Default: Enabled)
• SSH Authentication Timeout – Specifies the time interval in seconds that the
SSH server waits for a response from a client during an authentication attempt.
• (Range: 1 to 120 seconds; Default: 120 seconds)
• SSH Authentication Retries – Specifies the number of authentication attempts
that a client is allowed before authentication fails and the client has to restart the
authentication process. (Range: 1-5 times; Default: 3)
Web – Click Security, SSH, Settings. Enable SSH and adjust the authentication
parameters as required, then click Apply.


















