Campus Wireless Networks Validated Reference Design Version 3.3 | Design Guide Mobility Controller Configuration | 41
Role Derivation
Aruba uses the term ‘Role Derivation’ to describe the process of determining which role is to be
assigned to a user. The system can take into account the user’s credentials, location, time of day, and
authentication type when deciding which role to assign.
This system can be as detailed or as general as the administrator prefers. The Role Derivation process
determines:
z What class of service is provided to user traffic
z Which Firewall ACLs are applied to the user’s traffic
z Which VLAN the user is placed into
Secure Authentication Methods
The most common authentication methods for Campus WLANs are 802.1X, and Captive Portal; other
authentication methods are also discussed in this section. Mobility Controllers at the Aggregation Layer
are the central point of control for users and access points, and are typically deployed in the
distribution layer of the network. The Mobility Controllers sit in the authentication path, terminate
user-encrypted traffic, and enforce policy using the optional Aruba Policy Enforcement Firewall
module.
This ICSA certified stateful firewall allows control of user traffic as well as application awareness
through deep packet inspection. The Aruba Policy Enforcement Firewall module has the capacity to
dynamically follow sessions, log user sessions, and take actions through the blocking of user traffic and
blacklisting of users for policy violation. This Role-Based Access Control system allows users with
different access rights to share the same access points.
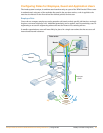
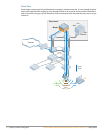
A wireless user gains access to the network by attempting to associate to the AP with the strongest
signal. The association request may have originated from a new user logging on to the network, or an
active user who has just roamed to a different location. The 802.11 MAC layer protocol association
request is forwarded to the Mobility Controller, which then attempts to retrieve the user’s state from the
active user database. If the user was not active previously, the Mobility Controller will proceed to
authenticate the user using 802.1X coupled with back-end authentications mechanisms such as
RADIUS, Active Directory or LDAP.
The Mobility Controller can perform user authentication in multiple ways to suit the varying needs of an
enterprise, and the existing AAA infrastructure in use. The most typical authentication methods
employed on Aruba networks can be summarized as:
z 802.1X based user authentication with a backend server
z 802.1X PEAP termination on the controller
z PPP based user authentication over IPSec based VPNs
z Captive Portal based user authentication
z A combination of authentication methods such as 802.1X followed by captive portal, or WEP
authentication followed by VPN
Authentication in the Aruba system typically leverages existing authentication stores, including
RADIUS, Active Directory, and LDAP. While the Aruba Mobility Controller does contain a scalable
Local DB for users and guests, it is typically desirable to have that functionality leveraged from an
existing authentication system to ease synchronization issues.