Campus Wireless Networks Validated Reference Design Version 3.3 | Design Guide Mobility Controller Configuration | 51
Role Variation by Authentication Method
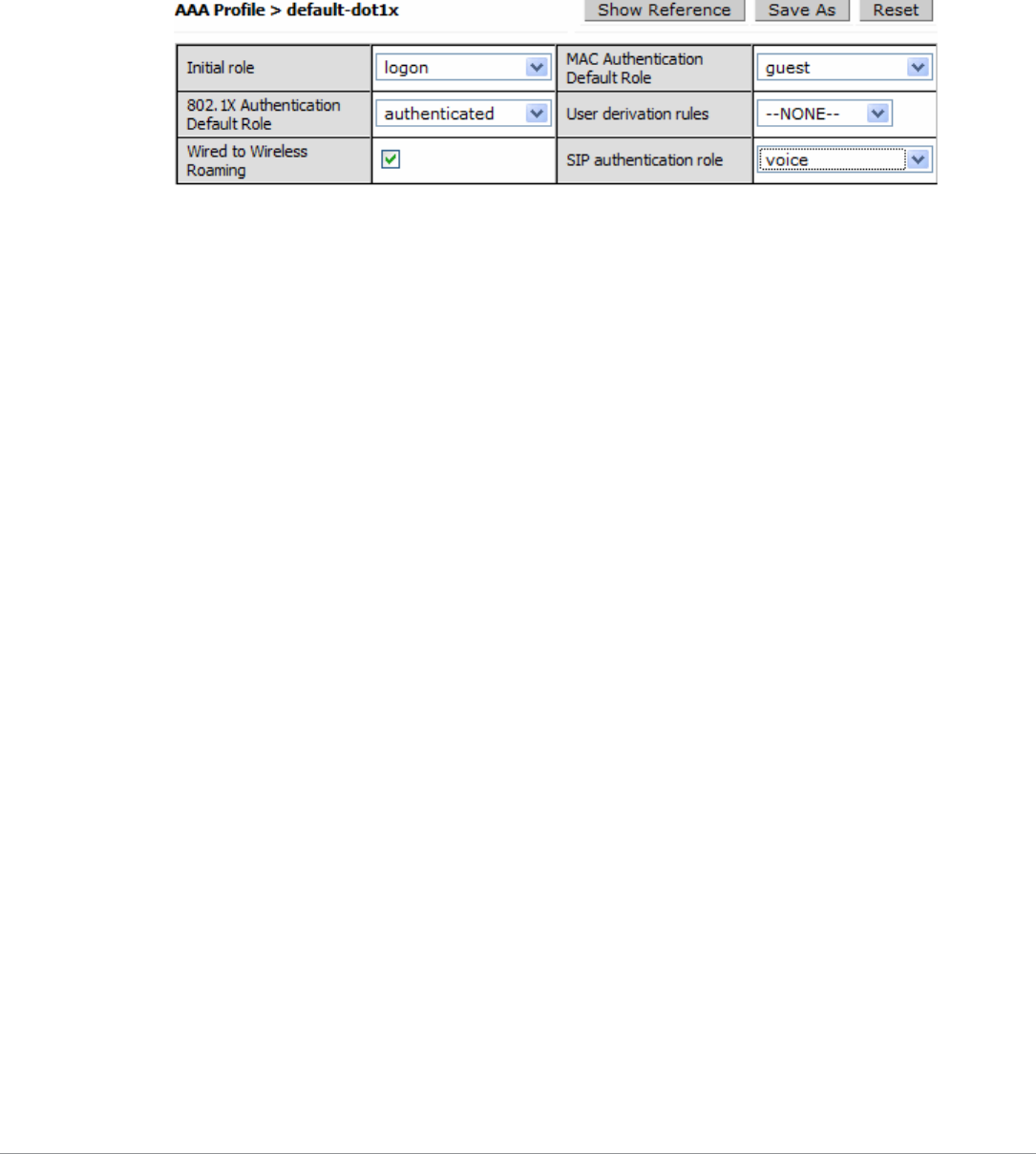
Role assignment has many options under the umbrella of role derivation. While the system can simply
use the role returned from the authentication server, it can also assign a role based on a number of
attributes. When a user logs in using WPA2 they receive an open employee role, but when logging in
with the same credentials using a captive portal, a reduced role is put into effect. Phones can share the
same authentication as a camera but receive a different voice role after completing registration with a
SIP server.
Wireless Intrusion Detection System
Due to the open nature of wireless networks they are prime targets for both unscrupulous individuals
and casual hackers that happen to live in the area. To protect against unsanctioned wireless devices,
use of Aruba’s Wireless Intrusion Detection System (WIDS) software module can automatically detect
and defend against wireless attacks and “rogue” APs on the network.
Wireless Attacks
A common wireless network attack is called “man-in-the-middle.” During such an attack, a hacker
masquerades as a legitimate AP using software on a laptop, and acting as a relay point, fools users and
other APs into sending data through the laptop instead of the real AP. The attacker can then eavesdrop
on conversations, modify or corrupt data, or run password-cracking routines.
Aruba Access Points monitor the air to detect other wireless stations masquerading as valid APs. When
masquerading is detected, appropriate defense mechanisms are put into place. Aruba Mobility
Controllers also track unique “signatures” for every wireless client in the network, and if a new station
is introduced claiming to be a particular client, but lacks a proper signature, a station impersonation
attack is declared.