7 Barracuda NG Network Access Client - Administrator’s Guide
The remediation server is the component from which policy attributes, such as firewall rule sets,
welcome messages, and bitmaps as well as client software components required for updates can be
obtained. It can be run on the same Barracuda NG Firewall system as the SHV or, for load balancing
reasons, it can be spread out over several Barracuda NG Firewall systems.
How does the client know at which address the SHV service component may be reached? There are
two options here. The first one is that the respective addresses are configured statically within the client
configuration on the endpoint. This approach is mandatory if DHCP based address assignment is not
used.
In the case of DHCP based address assignment the respective address or addresses are assigned to
the client by way of the vendor ID DHCP option (43).
DHCP is also used to make a distinction between own endpoint systems with an installed NG client
and the so called
guest systems. As guest systems are not able to communicate with SHV they are not
assigned any SHV addresses. By way of the DHCP user ID option sent by the client a DHCP server
may assign an address from a pool on a separate subnet.
Note that while this approach may easily be circumvented by a skilled human attacker to gain network
access, worm and other malware issued with limited intelligence located on visitor's notebooks are
typically prevented from quickly spreading out into the principal network.
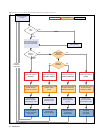
In this LAN scenario up to three firewall rule sets can be assigned to a secured and monitored
endpoint. When the endpoint system goes online and connects to the SHV it will be assigned a "local
machine" rule set and a "limited access" rule set. The limited access rule set is the one rule set that
comes into effect when the endpoint is diagnosed as unhealthy by the SHV. Note that the quarantine
state is not entered immediately as there is a configurable period of time during which the client is given
a chance to recover from the current condition, for example by successfully starting a disabled
anti-virus (AV) scanner service or updating an obsolete AV pattern file.
As soon as a user logs into the system a different policy may apply to the endpoint now, depending on
the identity of the user and various other conditions. The assigned policy attributes may in due cause
a different so-called "current user" rule set to be assigned. In contrast to the previous two this rule set
is volatile. That means it is cleared when the user logs off or the system is rebooted.
Consequently a notebook that has been used in the office environment and is taken home in the
evening will operate there with the most recently installed "local machine" firewall rule set.
Any endpoint whose system state is assessed as unhealthy will have the most recently installed
"limited access" rule set activated by the NG client after a configurable grace period.
Barracuda NG Network Access Client can also be used to secure mobile desktops connecting to the
corporate LAN through the internet. To this end, NG NAP provides an integrated VPN client. The VPN
client will establish a secure connection to a Barracuda NG VPN Service. The NG Network Access
Monitor will then communicate through the VPN tunnel with the responsible SHV. From this point on
the overall procedure is quite analogous to the LAN scenario. The most notable difference is that the
VPN server fully controls the virtual connection. That means that also traffic within the VPN network's
collision domain is fully subject to the NG Network Access Control framework. This better control also
necessitates that the remediation service component is also active on the very same Barracuda NG
Firewall system, which is also hosting the VPN Service.
In the LAN context certain policy attributes together with a "current user" rule set are assigned. This
setup supports a maximum of up to three different firewall rule sets. The rationale behind this
SHV and remediation server must always remain accessible to all endpoints regardless of the currently active
firewall rule set.