Installation
26 ETEP Installation Guide
Firewall Ports
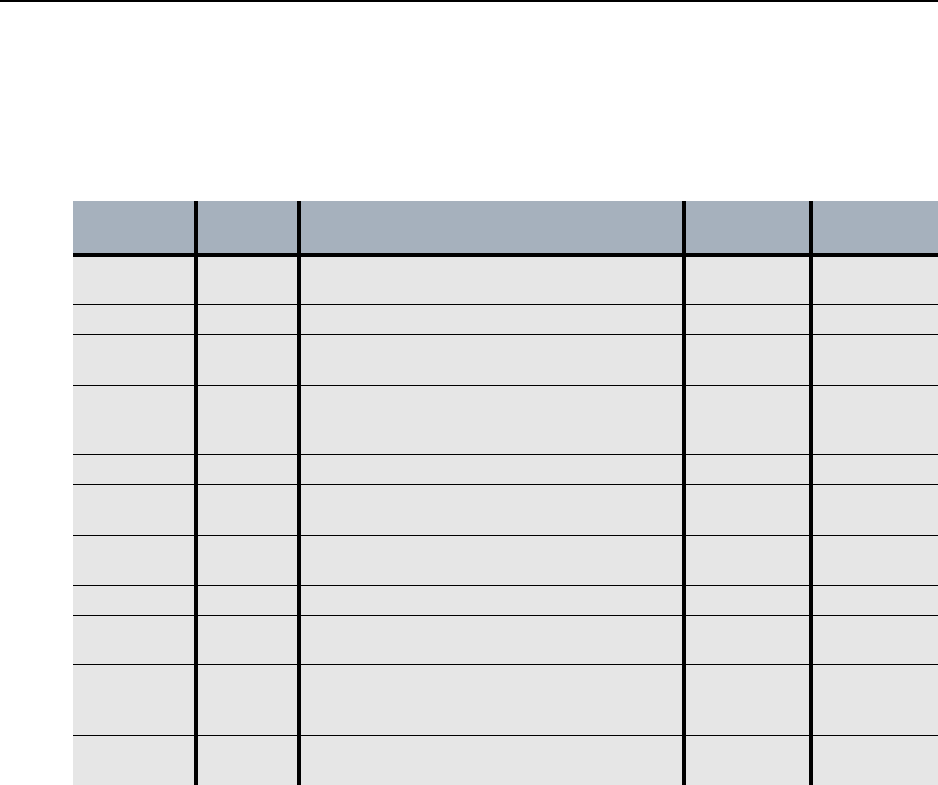
Table 10 lists the protocols that are used by the ETEPs and the EncrypTight system. Make sure that any
firewalls in your system are configured to allow for the protocols that are required for your deployment:
standalone ETEPs used for point-to-point encryption or ETEPs used in an EncrypTight system.
Installing the ET0010A
This section describes how to install ET0010A. To prepare the ET0010A for installation, review the
installation steps in Table 11, unpack the shipping carton, and prepare a space for the installation of the
appliance.
Table 10 Firewall ports
Protocol Port Description
Standalone
ETEPs
Cipher-
Engine
FTP TCP 20,
21
Used for upgrading the software on the
ETEP and retrieving appliance log files.
Yes Yes
ICMP/Ping Used to check connectivity with a device. Yes Yes
IKE /
ISAKMP
UDP 500 Used to establish security associations in
IKE policies.
Yes
IPSec ESP IP
protocol
50
Used in encryption policies. Yes Yes
SFTP TCP 22 Used for secure FTP operations. Yes Yes
SNMP UDP
161, 162
Used to send SNMP traps from the ETEPs
to a management workstation.
Yes
SNTP UDP 123 Used for time synchronization among
EncrypTight components.
Yes
SSH TCP 22 Used to securely access the CLI on ETEPs. Yes Yes
Syslog UDP 514 Used to send syslog messages from the
ETEPs to a syslog server.
Yes
TLS
(HTTPS)
TCP 443 A secure method of communicating
management information between ETEMS
and the ETEPs.
Yes
XML-RPC TCP 443 Used for communications between
EncrypTight components.
Yes


















