3
TKIP – Temporal Key Integrity Protocol is an
advanced encryption method using the RC4
algorithm. Instead of using the sequential IV, a
random IV will be used, and the IV key
definition will be updated regularly at a preset
time interval.
MIC – Message Integrity Check is an
encryption method used to prevent a hacker
from changing the data content. An
encryption algorithm and bit checksum at
both the sender and receiver ends are used
to check for alteration of the packet content.
5.1.3 Access Authorization
When the client is approved and authenti-
cated for a communication session, the client
receives a unique WEP key from the security
server, such as a RADIUS server, under the
802.1x/EAP authorization specification. A
new WEP key is issued for each connection,
thus improving security, and the WEP key is
updated regularly at a preset time interval.
Another method to screen out unauthorized
users is MAC address filtering.
ESS-ID – Extended Service Set Identification
is a type of unique identifier applied to both
the AP and the wireless client, as well as each
information packet. It allows APs to
recognize each wireless client and its traffic.
This option, however, does not provide
sufficient security for today’s wireless
networking environment. If the ESS-ID is set
to "any" or "null", anybody can connect to the
AP. Also, Windows XP automatically displays
the ESS-ID of the AP when a client receives a
"beacon." This is because APs transmit their
ESS-ID periodically and these transmissions
can be easily intercepted.
MAC Address – Media Access Control
address is a hardware address that uniquely
identifies network hardware such as a
wireless NIC or an AP. It is easy to access a
network with a stolen wireless NIC.
Although it is used as the top level filtering, it
is not secure enough, because MAC
addresses can be duplicated by non-
registered users.
5.1.4 IBSS Security
IBSS – Independent Basic Service Set
security is used for ad hoc communications
like the point-to-point protocol (PPP)
method. WEP and MAC address filtering can
be used at this point.
5.2 Integrity Features
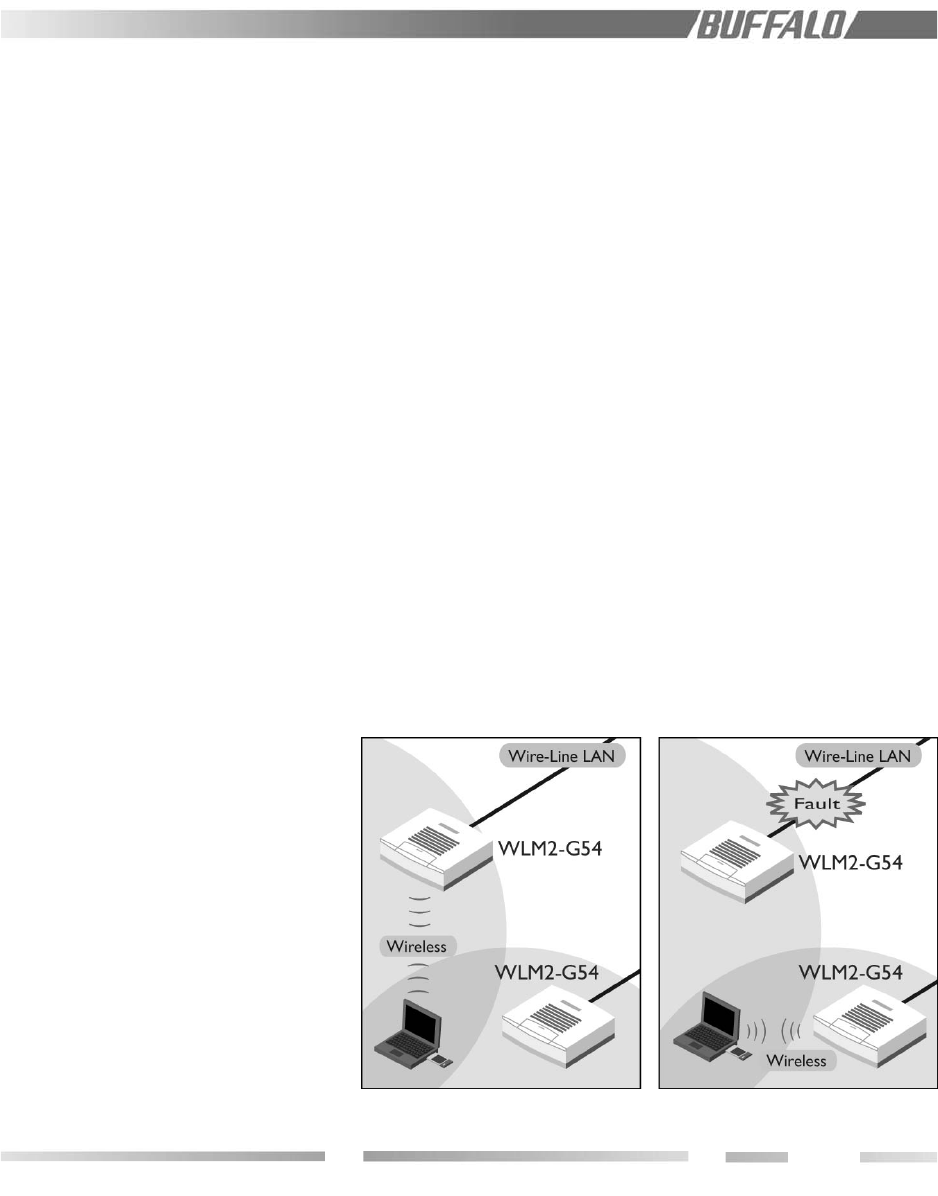
5.2.1 Improved Fault Tolerance
A company’s Intranet is an important
corporate communication backbone, so the
WLM2-G54 AP offers features for network
stability, which is achieved through the
system’s redundant switching function,
activated automatically in the event of faults.
The auto system redundancy provides the
network reliability necessary for mission
critical applications.
5.2.2 Link Integrity
When multiple access points use the same
frequency for roaming, they tend to interfere
with each other. The WLM2-G54 AP
automatically switches all PCs under the same
wireless ESS-ID to another available access
point if the current access point becomes
disconnected form the network, thus
preserving the connection and throughput.


















