13-29
Cisco IE 2000 Switch Software Configuration Guide
OL-25866-01
Chapter 13 Configuring IEEE 802.1x Port-Based Authentication
Information About Configuring IEEE 802.1x Port-Based Authentication
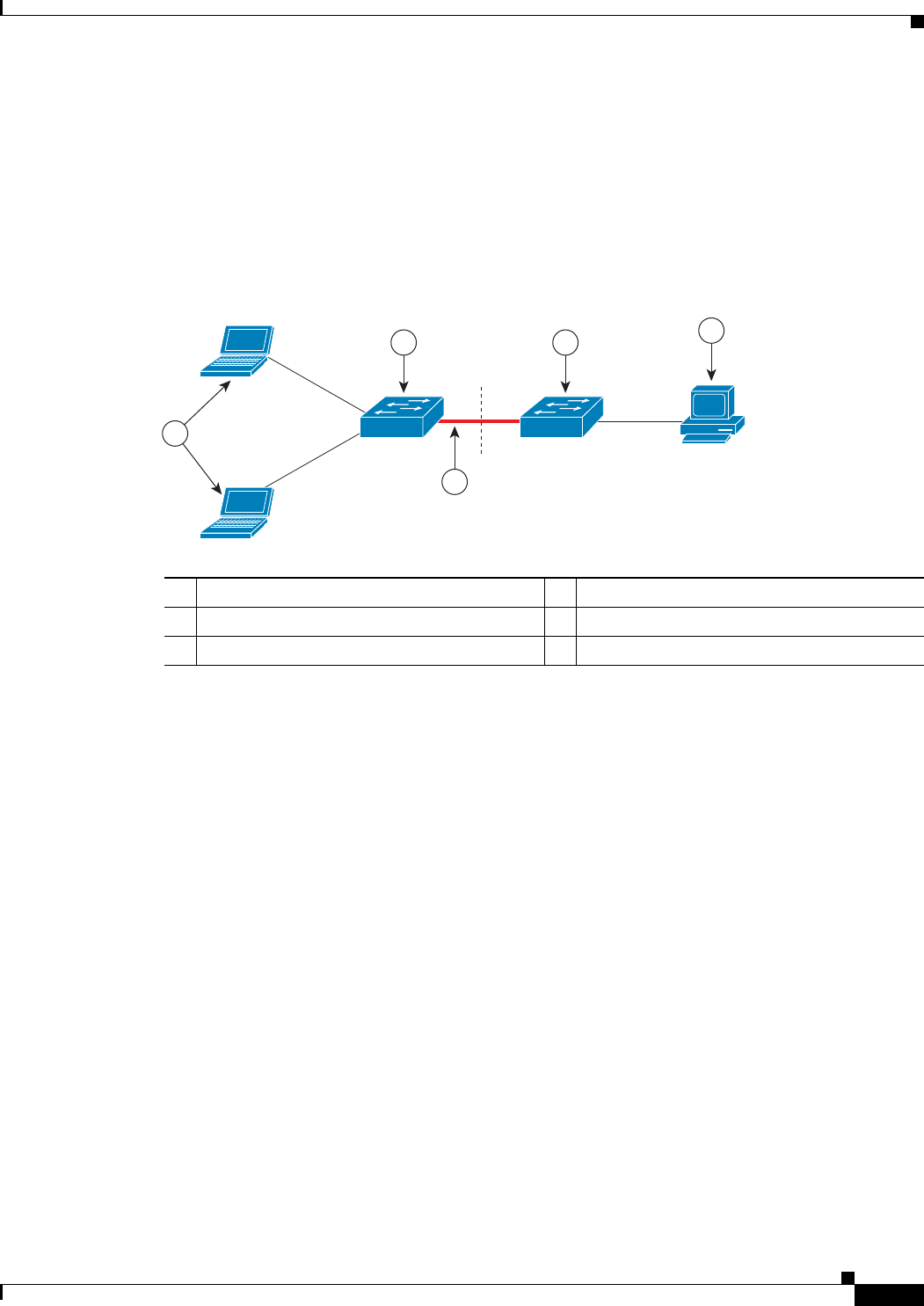
• Host authorization ensures that only traffic from authorized hosts (connecting to the switch with
supplicant) is allowed on the network. The switches use Client Information Signalling Protocol
(CISP) to send the MAC addresses connecting to the supplicant switch to the authenticator switch,
as shown in
Figure 13-6.
• Auto enablement automatically enables trunk configuration on the authenticator switch, allowing
user traffic from multiple VLANs coming from supplicant switches. Configure the cisco-av-pair as
device-traffic-class=switch at the ACS. (You can configure this under the group or the user settings.)
Figure 13-6 Authenticator and Supplicant Switch using CISP
802.1x Supplicant and Authenticator Switch Guidelines
• You can configure NEAT ports with the same configurations as the other authentication ports. When
the supplicant switch authenticates, the port mode is changed from access to trunk based on the
switch vendor-specific attributes (VSAs). (device-traffic-class=switch)
• The VSA changes the authenticator switch port mode from access to trunk and enables 802.1x trunk
encapsulation and the access VLAN if any would be converted to a native trunk VLAN. VSA does
not change any of the port configurations on the supplicant
• To change the host mode and to apply a standard port configuration on the authenticator switch port,
you can also use Auto Smartports user-defined macros, instead of the switch VSA. This allows you
to remove unsupported configurations on the authenticator switch port and to change the port mode
from access to trunk. For information, see the AutoSmartports Configuration Guide.
For more information, see the “Configuring an Authenticator” section on page 13-47.
Using IEEE 802.1x Authentication with ACLs and the RADIUS Filter-Id Attribute
The switch supports both IP standard and IP extended port access control lists (ACLs) applied to ingress
ports.
• ACLs that you configure
• ACLs from the Access Control Server (ACS)
1 Workstations (clients) 2 Supplicant switch (outside wiring closet)
3 Authenticator switch 4 Access control server (ACS)
5 Trunk port
205718
1
2 3
5
4


















