Reference Manual for the 54 Mbps Wireless Router WGR614 v4
3-2 Wireless Configuration
December 2003
Implement Appropriate Wireless Security
Unlike wired network data, your wireless data transmissions can be received well beyond your
walls by anyone with a compatible adapter. For this reason, use the security features of your
wireless equipment. The WGR614 v4 router provides highly effective security features which are
covered in detail in this chapter. Deploy the security features appropriate to your needs.
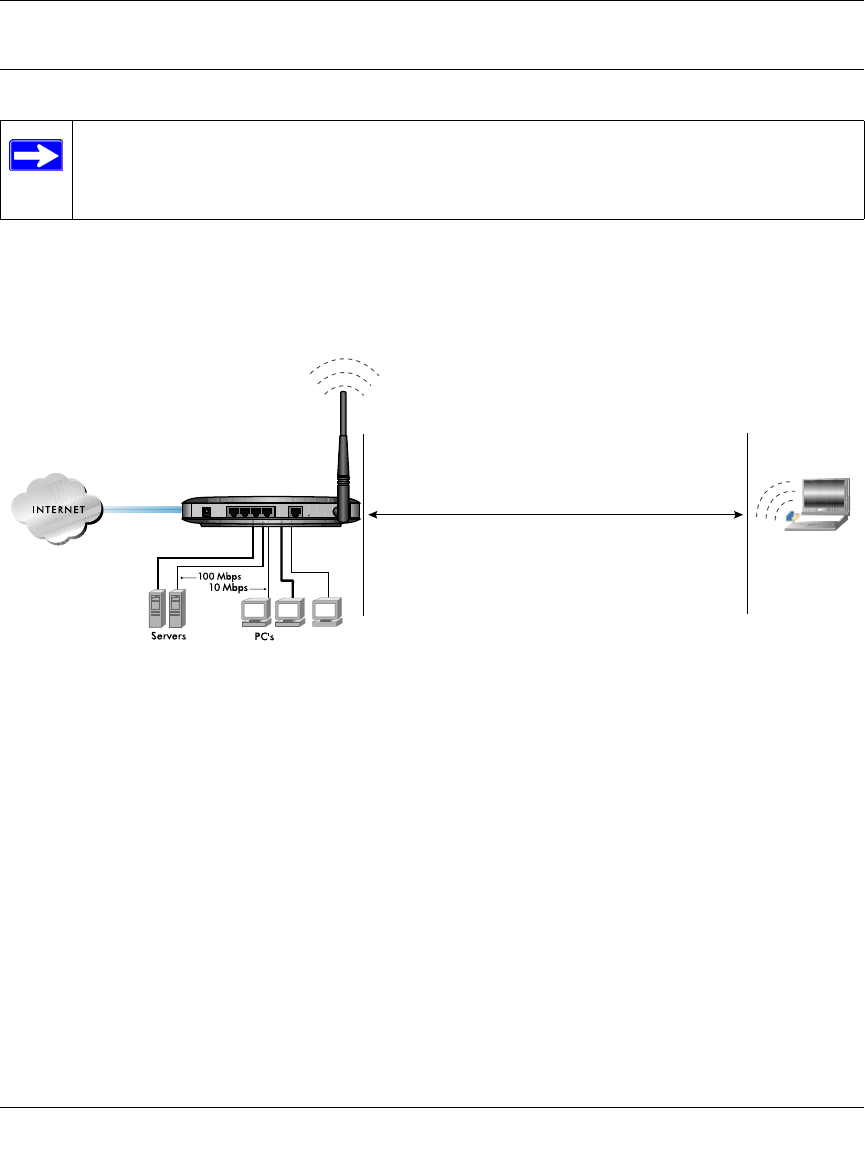
Figure 3-1: WGR614 v4 wireless data security options
There are several ways you can enhance the security of you wireless network.
• Restrict Access Based on MAC address. You can restrict access to only trusted PCs o that
unknown PCs cannot wirelessly connect to the WGR614 v4. MAC address filtering adds an
obstacle against unwanted access to your network, but the data broadcast over the wireless link
is fully exposed.
• Turn Off the Broadcast of the Wireless Network Name SSID. If you disable broadcast of
the SSID, only devices that have the correct SSID can connect. This nullifies the wireless
network ‘discovery’ feature of some products such as Windows XP, but the data is still fully
exposed to a determined snoop using specialized test equipment like wireless sniffers.
• WEP. Wired Equivalent Privacy (WEP) data encryption provides data security. WEP Shared
Key authentication and WEP data encryption will block all but the most determined
eavesdropper.
Note: Indoors, computers can connect over 802.11b/g wireless networks at
ranges of up to 500 feet. Such distances can allow for others outside of your
immediate area to access your network.
1) Open System: Easy but no security
2) MAC Access List: No data security
3) WEP: Security but some performance impact
Wireless Data
Security Options
Range: Up to 300 Foot Radius
WGR614 v4


















