ZyXEL G-270S User’s Guide
Chapter 3 ZyXEL Utility Configuration 41
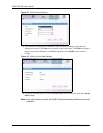
Figure 15 Security Settings: WPA-PSK/WPA2-PSK
The following table describes the labels in this screen.
3.2.2.4 802.1x
Figure 16 Security Settings: 802.1x
Table 8 Security Settings: WPA-PSK/WPA2-PSK
LABEL DESCRIPTION
Security Setting
Encryption Type The encryption mechanisms used for WPA/WPA2 and WPA-PSK/WPA2-PSK are
the same. The only difference between the two is that WPA-PSK/WPA2-PSK uses
a simple common password, instead of user-specific credentials.
The encryption types for WPA-PSK and WPA2-PSK are TKIP and AES
respectively. Refer to Section 2.2.3 on page 27 for more information.
Pass Phrase Type a passphrase from 8 to 63 case-sensitive ASCII characters (including spaces
and symbols).
Back Click Back to go to the Site Survey screen to select and connect to other network.
Next Click Next to confirm your selections and advance to the Confirm Save screen.
Refer to Section 3.2.3 on page 42.
Exit Click Exit to return to the Site Survey screen without saving.