Tunneling 2-5
Tunneling
This section describes tunneling, the method by
which Token Ring frames are encapsulated (embed-
ded) within Ethernet frames.
Frames are sets of bits that form an elementary block
of data to be sent over a communications channel. A
frame contains its own control information, including
the transmission address and data for error detection.
This header information makes certain that the
frames arrive with their payload (user data) intact and
at the right destination. Simply put, what tunneling
does is to take a Token Ring frame and embed it into
an Ethernet frame to be sent over a Fast Ethernet net-
work.
Requirements
The tunneling scheme must be compatible with Fast
Ethernet networks so that a mix of Ethernet, 802.3,
and the Ethernet/Token Ring (E/TR) frames may reside
on the same segment without interference. It is also
important that any end station (server, bridge, router)
be able to reassemble the original TR frame. Source
routing from Token Ring to Ethernet and back to
Token Ring should be supported.
Token Ring Frames
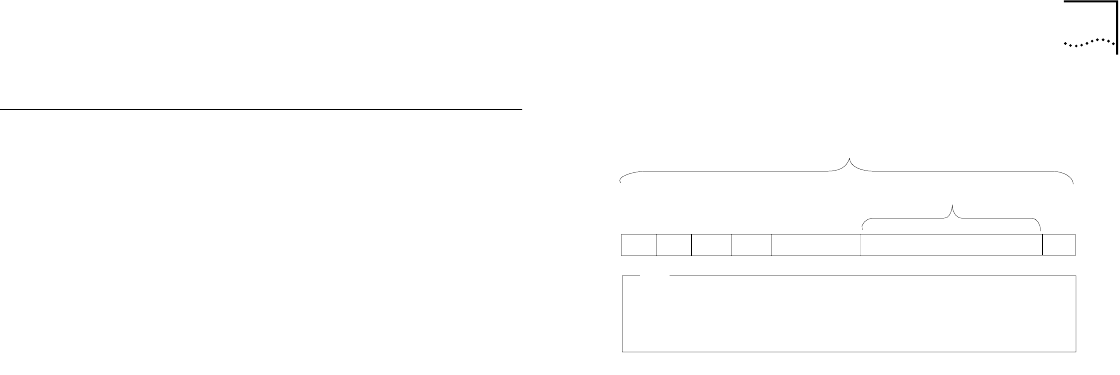
Figure 2-3 shows a simplified drawing of a Token Ring
frame.
Figure 2-3 Token Ring Frame.
The Token Ring frame must be specially tagged when
preparing it for embedding inside the Ethernet frame.
Tagging allows an Ethernet frame to carry:
■ User priority information over media types other-
wise unable to signal priority information
■ Token Ring data in native format (802.5) over
non-802.5 media
■ VLAN identification information
Tagging requires the addition of a tag header to each
frame. This header is inserted immediately following
the Destination Address (DA), Source Address (SA),
and, if present, the Routing Information Field (RIF). If
the source and destination media differ, tagging the
frame may involve translation or encapsulation of the
frame remainder. Tagging also requires re-computa-
tion of the Frame Check Sequence (FCS), which are
extra characters added to frames for error control
purposes.
AC
FC nDA
nSA RIF (optional) User Data
Token Ring Header Information
Payload
Key
AC–Access Control Field
FC–Frame Control Field
nDA–Non-canonical Destination
Address Field
nSA–Non-canonical Source
Address Field
RIF–Route Information Field
FCS
FCS–Frame Check Sequence


















