50 CHAPTER 4: USING THE CENTRAL CONFIGURATION MANAGER
RADIUS clients. The authenticator controls port access for the network client
devices connected to the switch.
When the option is set to Disable 802.1X, all packets are processed as a normal
Ethernet switch; no 802.1X control applies.
With Standard 802.1X selected, control is enabled. Once the device is authorized,
the port it connects to is in the authorized state and all packets entering the port
are allowed to pass through.
When the Secure 802.1X option is selected, control is enabled. In addition, the
IntelliJack will check its ATU to determine if packets entering the port should be
forwarded. If the device is authorized, the IntelliJack will put the MAC address of
the device in the ATU and allow its packets to pass through. The NJ220 will block
all other packets that don’t have the correct MAC address specified in the ATU.
You can select the MAC address filter option if a client device does not support
802.1X and wishes to connect to the network through the IntelliJack (e.g., a
network printer). In this case, you can manually add the device’s MAC address
associated to the port in the ATU, and packets from the network to this port will
be blocked unless their MAC addresses are listed in the ATU.
802.1X with IP Phone is a special case of 802.1X secure mode. In this mode, when
a 3Com IP phone is connected to the IntelliJack, the phone’s MAC address will be
locked into the ATU automatically. Therefore, packets sent from the phone can
pass through by default without further authentication. If 802.1X control is not
required, an IP phone can connect to a port with 802.1X disabled and voice traffic
will pass through without authentication.
24 When 802.1X security is applied, authentication is required and reauthentication
is required at specific intervals. The IntelliJack disables reauthentication by default.
When reauthentication is enabled, the default period is 3600 seconds. You could
select an interval ranging from 10 to 65535 seconds. If you prefer that a
supplicant device authenticates itself on a frequent basis, you would choose a
small reauthentication interval. Likewise, you would increase the interval or disable
the function if you were not concerned about regular authentication of the
devices on your network.
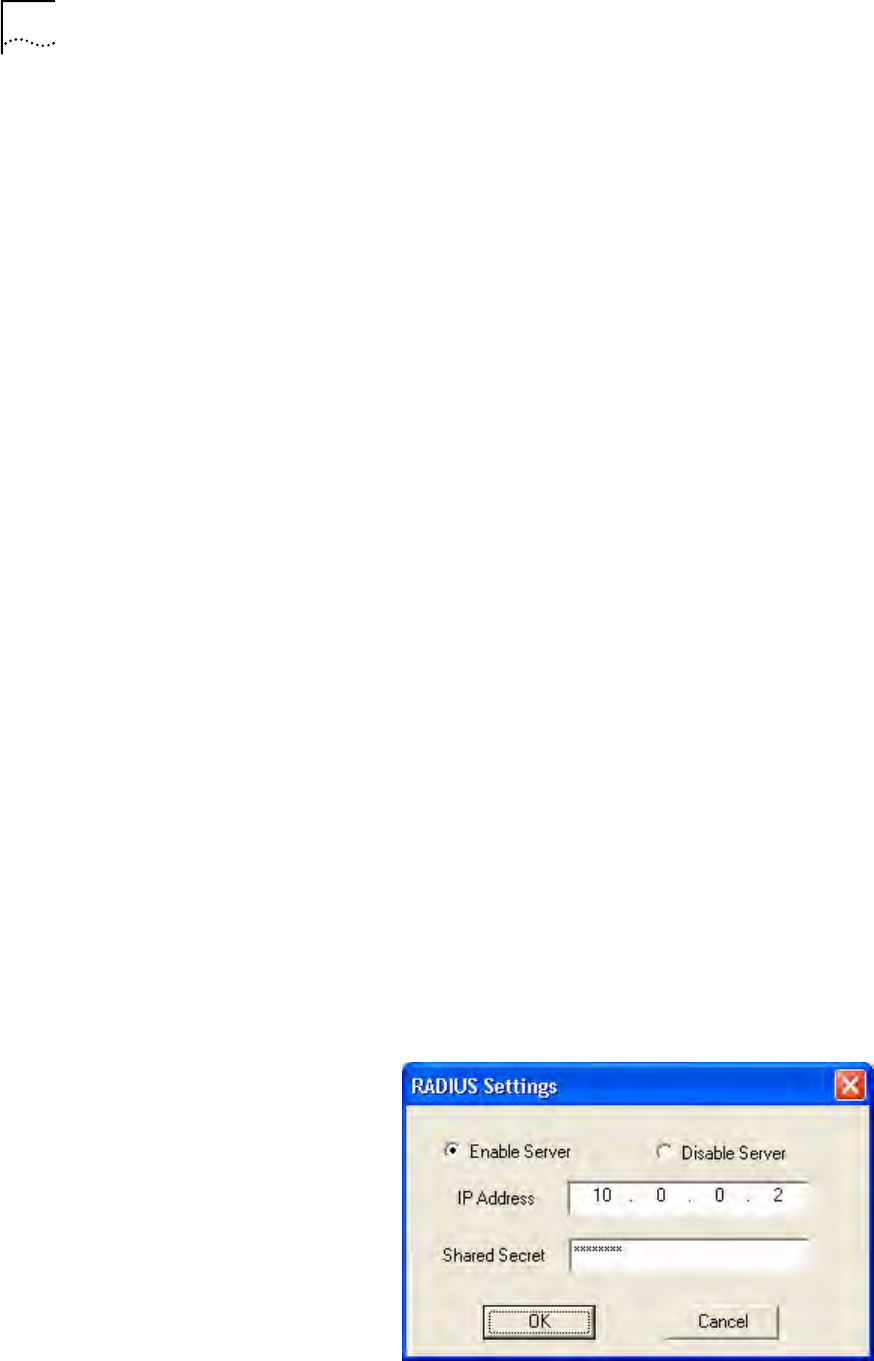
25 To use 802.1X, you must select a RADIUS server to act as authenticator to devices
connected to the NJ220. To select a Primary or Secondary RADIUS server, click the
box and the Configure button. This will open a separate window.
In this box you can Enable or Disable the server, enter the server’s IP address and
the Shared Secret.