Vigor2910 Series User’s Guide
124
3
3
.
.
1
1
1
1
W
W
i
i
r
r
e
e
l
l
e
e
s
s
s
s
L
L
A
A
N
N
This function is used for G models only.
3
3
.
.
1
1
1
1
.
.
1
1
B
B
a
a
s
s
i
i
c
c
C
C
o
o
n
n
c
c
e
e
p
p
t
t
s
s
Over recent years, the market for wireless communications has enjoyed tremendous growth.
Wireless technology now reaches or is capable of reaching virtually every location on the
surface of the earth. Hundreds of millions of people exchange information every day via
wireless communication products. The Vigor G model, a.k.a. Vigor wireless router, is
designed for maximum flexibility and efficiency of a small office/home. Any authorized
staff can bring a built-in WLAN client PDA or notebook into a meeting room for conference
without laying a clot of LAN cable or drilling holes everywhere. Wireless LAN enables high
mobility so WLAN users can simultaneously access all LAN facilities just like on a wired
LAN as well as Internet access.
The Vigor wireless routers are equipped with a wireless LAN interface compliant with the
standard IEEE 802.11g protocol. To boost its performance further, the Vigor Router is also
loaded with advanced wireless technology Super G
TM
to lift up data rate up to 108 Mbps*.
Hence, you can finally smoothly enjoy stream music and video.
Note: * The actual data throughput will vary according to the network conditions
and environmental factors, including volume of network traffic, network
overhead and building materials.
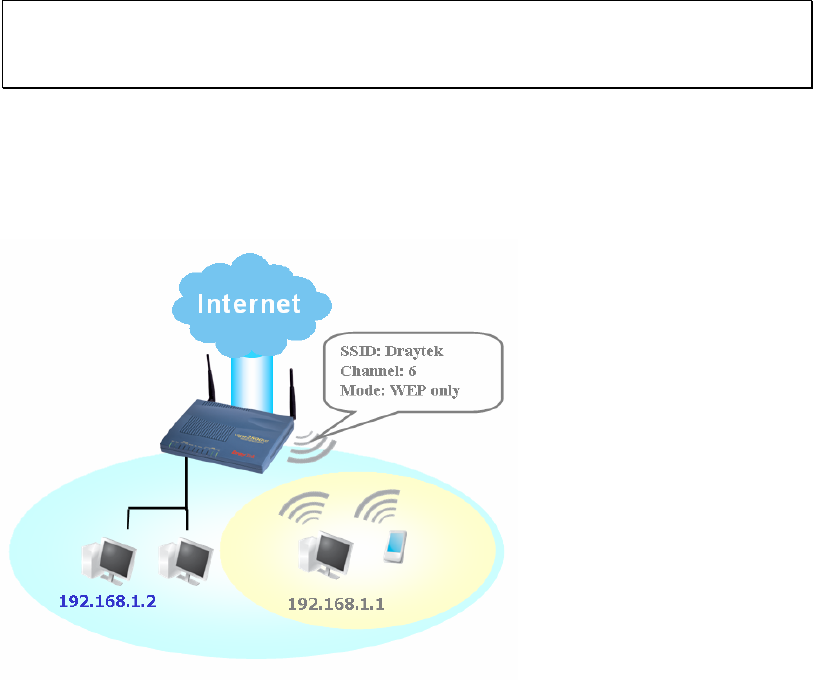
In an Infrastructure Mode of wireless network, Vigor wireless router plays a role as an
Access Point (AP) connecting to lots of wireless clients or Stations (STA). All the STAs will
share the same Internet connection via Vigor wireless router. The General Settings will set
up the information of this wireless network, including its SSID as identification, located
channel etc.
S
S
e
e
c
c
u
u
r
r
i
i
t
t
y
y
O
O
v
v
e
e
r
r
v
v
i
i
e
e
w
w
Real-time Hardware Encryption: Vigor Router is equipped with a hardware AES
encryption engine so it can apply the highest protection to your data without influencing user
experience.
Complete Security Standard Selection: To ensure the security and privacy of your wireless
communication, we provide several prevailing standards on market.


















