70 SPARC Enterprise Mx000 Servers Administration Guide • April 2007
All connections established through log archiving are encrypted. The log archiving
feature provides the ability to use an RSA public key to authenticate the archive
host. You manage this public key on the Service Processor.
By default, log archiving is disabled. To use log archiving, you set up an archive
host, and then enable log archiving on the Service Processor.
When enabled, log archiving periodically uses the secure copy program (scp)to
transfer new log data to the archive host. Log archiving uses ssh to monitor the disk
space consumed by archives. It deletes old archives when necessary, so that the
space consumed by the archives will never exceed user-configurable archive space
limits. However, for security reasons, log archiving does not automatically delete
audit log archives. You can manually delete audit log archives that are no longer
needed.
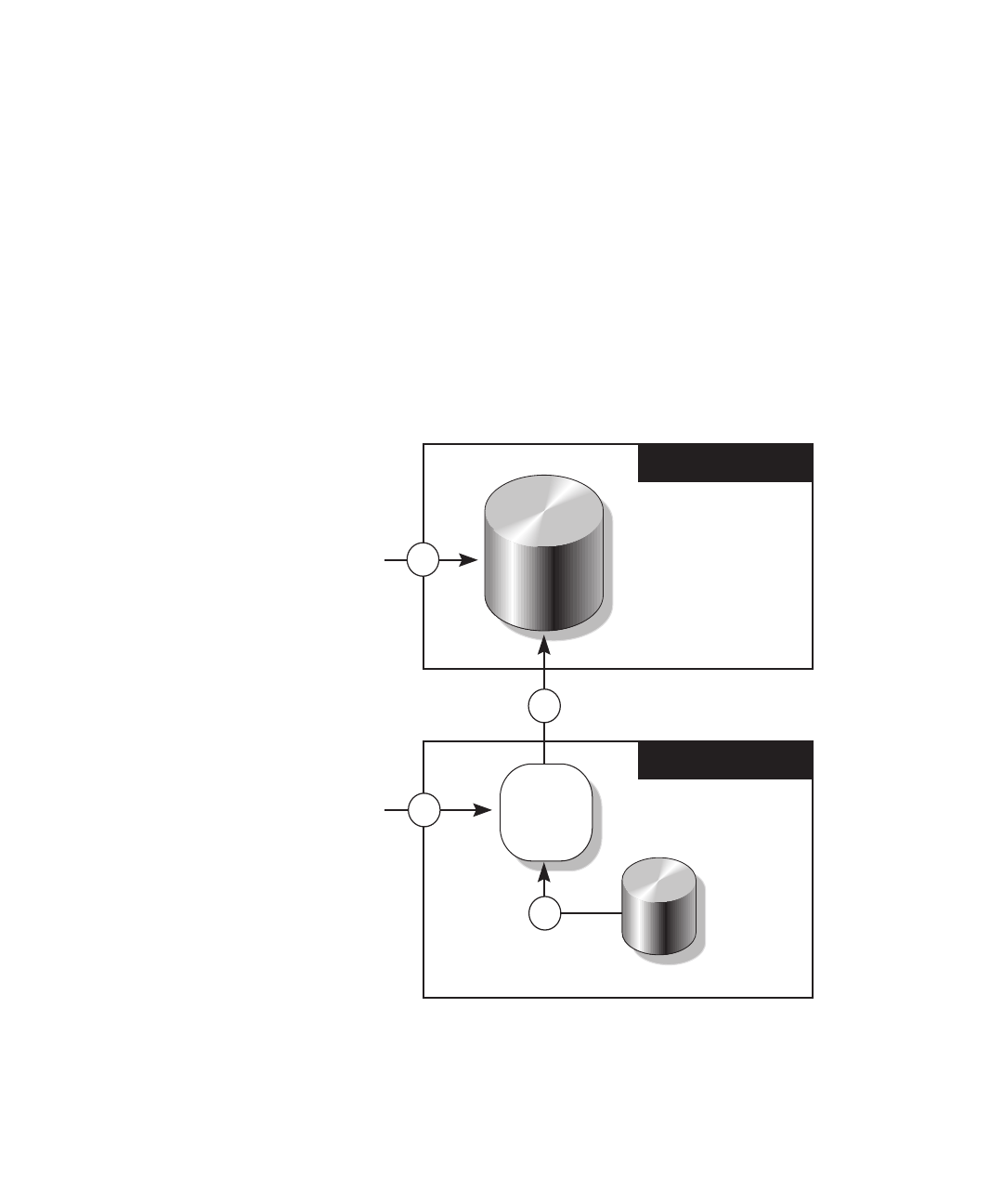
FIGURE 6-1 illustrates how log archiving works.
FIGURE 6-1 Log Archiving
User Interface
on Archive Host
User Interface
on Service
Processor
Archive Host
Service Processor
Archive
Directory
Log
Archiving
Logs
1
2
4
3


















