7.3.2 SSL Certificates
HTTPS is not a protocol itself, but it actually refers to HTTP communication over SSL (Secure Sockets
Layer) connection. HTTPS uses public-key cryptography to protect the communication. With HTTPS, the
server sends back its identification in the form of a digital certificate. The certificate usually contains
the server name, the trusted certificate authority (CA), and the server's public encryption key.
The server certificate includes a digital signature from a certification authority. Each browser is normally
equipped with a set of CA root certificates of commercial authorities. The web browsers perform a set of
verifications over the digital certificate in order to validate the certificate and start the HTTPS
communication. The main checks are substantially the following:
• The client verifies that the issuing Certificate Authority (CA) is on its list of trusted CAs.
• The client checks the server's certificate validity period
Further to this, the client may compare the actual DNS name of the server to the DNS name on the
certificate (though this last point may be browser dependent).
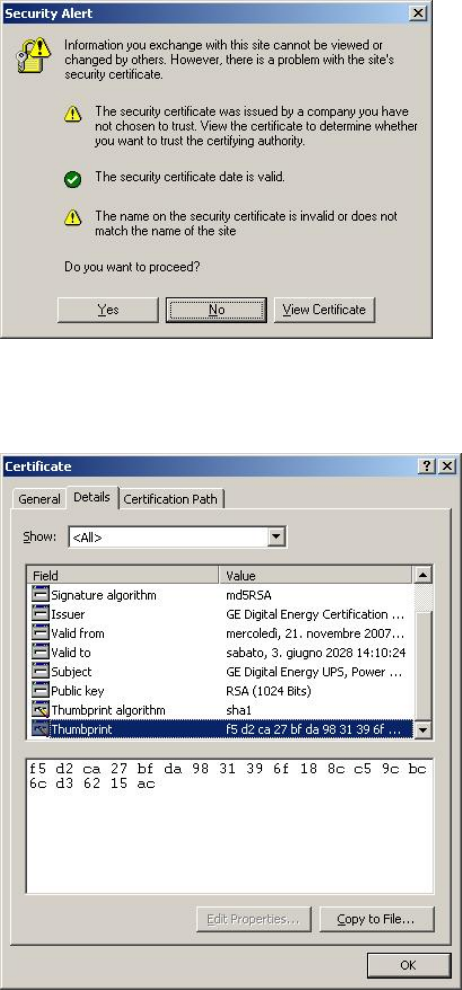
Below is a sample of the results of these checks, when browser attempts to establish an HTTP
connection to the web server embedded in the SNMP/Web adapter (the sample is take from Internet
Explorer, but similar indications can be obtained with the most common browsers):
First of all, in order to verify the actual certificate, its fingerprint (sometimes also knows as thumbprint)
can be checked against the one provided by the SNMP/Web adapter. Particularly, select View Certificate
and look for the fingerprint/thumbprint:
Modifications reserved Page 47/58
OPM_CNT_SNM_BAS_CRD_1GB_V012.doc Operating Manual SNMP/Web Adapter


















