TACACS+ Authentication
How Authentication Operates
To delete a per-server encryption key in the switch, re-enter the tacacs-server
host command without the key parameter. For example, if you have
north01
configured as the encryption key for a TACACS+ server with an IP address of
10.28.227.104 and you want to eliminate the key, you would use this command:
HPswitch(config)# tacacs-server host 10.28.227.104
Note- The show tacacs command lists the global encryption key, if configured.
However, to view any configured per-server encryption keys, you must use
show config or show config running (if you have made TACACS+ configuration
changes without executing
write mem).
Configuring the Timeout Period. The timeout period specifies how long
the switch waits for a response to an authentication request from a TACACS+
server before either sending a new request to the next server in the switch’s
Server IP Address list or using the local authentication option. For example,
to change the timeout period from 5 seconds (the default) to 3 seconds:
HPswitch(config)# tacacs-server timeout 3
How Authentication Operates
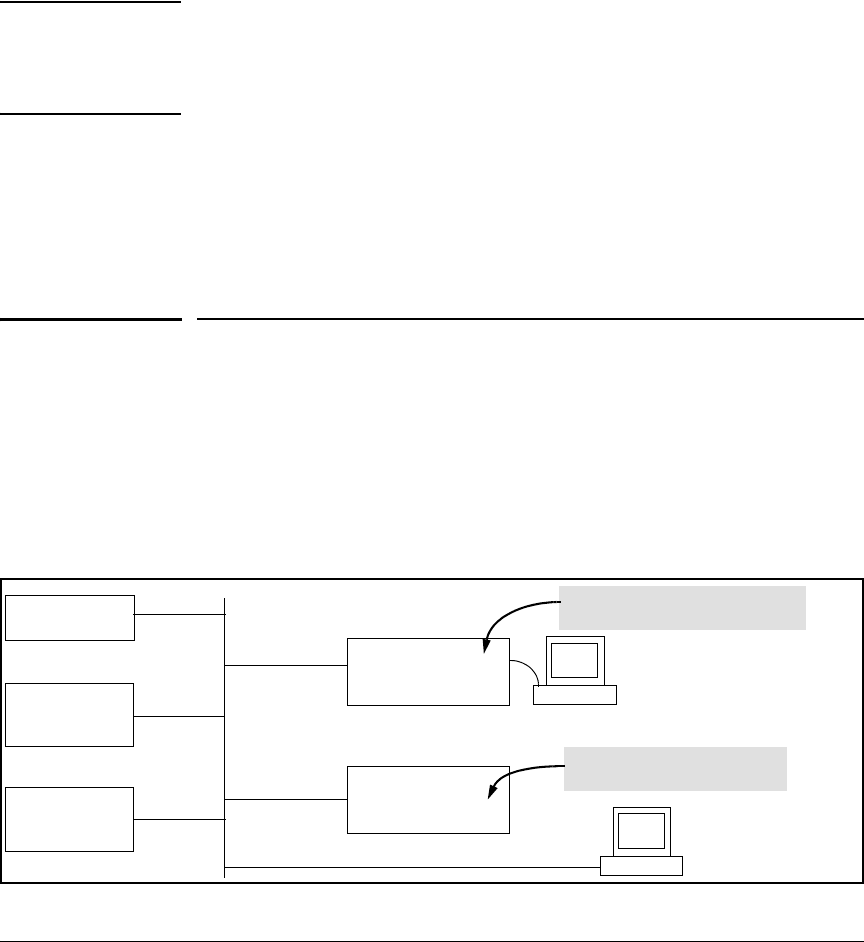
General Authentication Process Using a TACACS+
Server
Authentication through a TACACS+ server operates generally as described
below. For specific operating details, refer to the documentation you received
with your TACACS+ server application.
HP Switch Configured
for TACACS+ Operation
First-Choice
TACACS+ Server
B
HP Switch
Configured for
TACACS+ Operation
Terminal “A” Directly Accessing This
Switch Via Switch’s Console Port
Terminal “B” Remotely
Accessing This Switch Via Telnet
A
Second-Choice
TACACS+ Server
(Optional)
Third-Choice
TACACS+ Server
(Optional)
Figure 4-6. Using a TACACS+ Server for Authentication
4-20


















