ISA Server 2004 Configuration Guide 132
Rule Element Value
Order (priority) 1
Action Allow
Protocols HTTP and FTP (download).
From/Listener Internal Network.
To www.microsoft.com and ftp.microsoft.com.
Condition Limited Web Access (Group).
This rule limits allows users that belong to the Limited Web Access group to use the HTTP
and FTP (download) protocols. However, members of that group must be located on the
internal network when they issue the request. In addition, not only must the members of the
Limited Web Access be located on the internal network when they issue an HTTP or FTP
(download) request, they can only access the www.microsoft.com and ftp.microsoft.com sites
when using the protocols. This prevents users from putting the network at risk by downloading
content from other Web sites which may contain untrusted or dangerous content.
The first step to strong user/group-based outbound access control is configuring the client
systems behind the ISA Server 2004 firewall as Firewall and Web Proxy clients. Only Firewall
and Web Proxy clients can authenticate with the firewall. By contrast, SecureNAT clients are
not able to authenticate. Outbound access control is limited by the source IP address.
In Chapter 10 of the ISA Server 2004 Configuration Guide, you configured the CLIENT
machine on the internal network as a SecureNAT, Firewall and Web Proxy client. This
configuration enables the machine to send credentials to the ISA Server 2004 so that strong
user/group-based Access Rules can be created.
In this chapter, you will create several Access Rules that control outbound access through the
ISA Server 2004 firewall. Two rules are based on user/group membership, and one rule will
control outbound access based on the source IP address of a server on the internal network.
You will perform the following procedures to create the customized firewall policy:
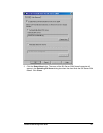
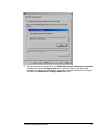
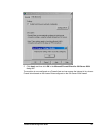
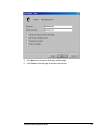
• Create a user account
• Disable the Access Rules created by the Network Template
• Create an Access Rule limiting protocols and sites users can access
• Create an Access Rule that provides administrators greater access to protocols and
sites
• Create a DNS server Access Rule allowing the Internal network DNS server access
to Internet DNS servers
• Use HTTP Policy to prevent access to suspect Web sites
• Test the Access Rules