RSA RADIUS Server 6.1 Administrator’s Guide About RSA RADIUS Server 3
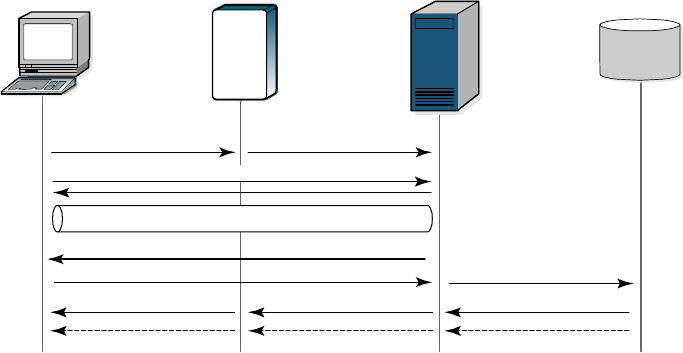
Figure 1 RSA RADIUS Authentication
1A RADIUS access client, who could be a dial-in user, a mobile user with
wireless network access, or someone working at a remote office, sends an
authentication request to a remote access server (RAS), which might be a wireless
Access Point, an ISDN bridge, or a modem pool.
NOTE: The terms “remote access server” (RAS) and “network access server”
(NAS) are interchangeable. This manual uses RAS, though some attribute
names and parameters retain the older ‘NAS’ in their names.
2 When the RAS receives a user’s connection request, it performs an initial
access negotiation with the user to establish connection information. It
forwards this information to the RSA RADIUS server, which uses the
information to create a tunnel between itself and the access client.
3 The RSA RADIUS server sends a request for the user’s credentials through
the TTLS tunnel.
4 The access client sends a user ID and passcode (tokencode and personal
identification number) to the RSA RADIUS server.
5 The RSA RADIUS server forwards the user’s user ID and passcode to the
RSA Authentication Manager, which verifies that the user ID exists and that
the passcode is correct for that user at that specific time.
6 If the user’s information is accepted, the RSA Authentication Manager
returns a message indicating that the passcode is accepted (6a). The
RSA Authentication Manager may also return the name of the profile
associated with this user in the Access-Accept message.
Access
Client
RSA
RADIUS
Server
RSA
Authentication
Manager
1. Connection Request
Connection Notification
2. TTLS/PAP Tunnel Negotiation
5. User ID/Passcode
6a. Passcode Accepted (Profile Name)
6b. Passcode Rejected
7a. Access-Accept (Attributes)
7b. Access-Reject
8a. Connection Accepted
8b. Connection Refused
3. User ID/Passcode?
4. User ID/Passcode
Remote
Access
Server
TTLS/PAP Tunnel


















