Chapter 2 Wireless LANs
NWD-270N User’s Guide
23
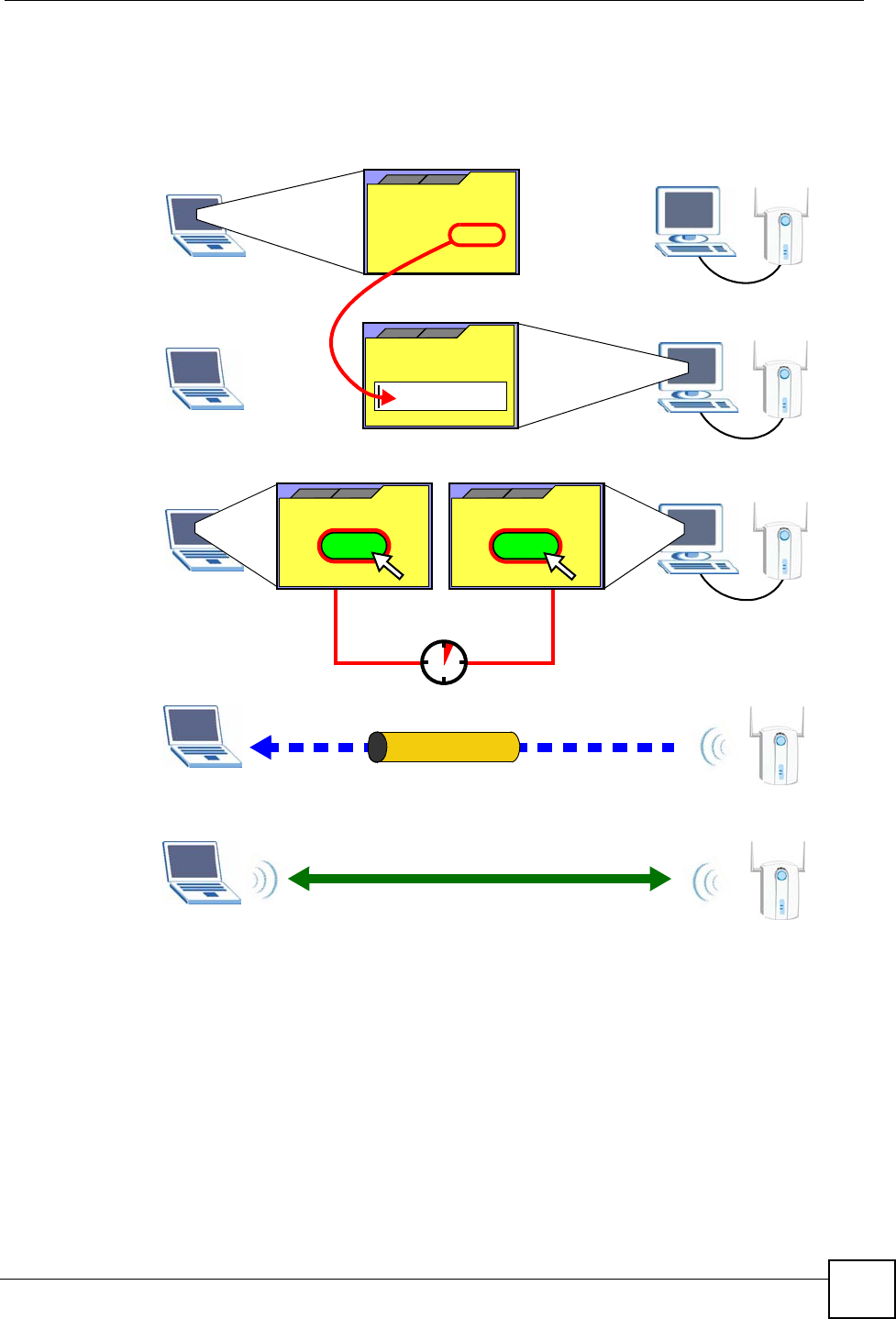
The following figure shows a WPS-enabled wireless client (installed in a notebook computer)
connecting to the WPS-enabled AP via the PIN method.
Figure 5 Example WPS Process: PIN Method
2.4.3 How WPS Works
When two WPS-enabled devices connect, each device must assume a specific role. One device
acts as the Registrar (the device that supplies network and security settings) and the other
device acts as the Enrollee (the device that receives network and security settings. The
registrar creates a secure EAP (Extensible Authentication Protocol) tunnel and sends the
network name (SSID) and the WPA-PSK or WPA2-PSK pre-shared key to the enrollee.
Whether WPA-PSK or WPA2-PSK is used depends on the standards supported by the devices.
If the registrar is already part of a network, it sends the existing information. If not, it generates
the SSID and WPA(2)-PSK randomly.
ENROLLEE
SECURE EAP TUNNEL
SSID
WPA(2)-PSK
WITHIN 2 MINUTES
COMMUNICATION
This device’s
WPS
Enter WPS PIN
WPS
from other device:
WPS PIN: 123456
WPS
START
WPS
START
REGISTRAR


















