Product Overview
10 ETEP Installation Guide
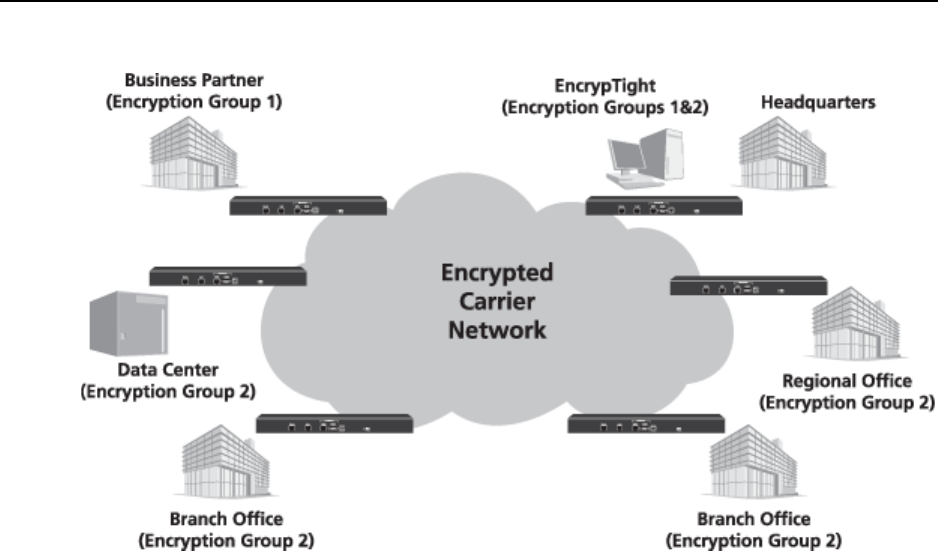
Figure 1 Multipoint Ethernet Encryption using EncrypTight
The ETEP interfaces with network equipment through two data ports, the local port and the remote port.
Unencrypted traffic that originates from a trusted, local network is received on the local port, where the
ETEP applies security processing to it. The encrypted traffic is then sent from the remote port to an
untrusted network such as the Internet. At the opposite endpoint the process is reversed. Encrypted traffic
is received on the ETEP remote port and decrypted. Then the decrypted traffic is sent from the local port
to the destination.
The ETEP is managed in-line or out-of-band through a dedicated Ethernet management interface. The
ETEP can be managed in two ways, depending on the size and complexity of your deployment:
● Command Line Interface (CLI)
The CLI is all you need to manage a standalone deployment, typically a pair of ETEPs. CLI
commands are available to perform initial setup of the ETEP, along with diagnostic and
troubleshooting commands. In Layer 2 deployments, you can configure the ETEPs for operation and
create Layer 2 point-to-point policies using the CLI commands.
● EncrypTight Policy and Key Manager™
EncrypTight is an application for managing group encryption deployments. EncrypTight separates the
functions of policy management, key generation and distribution, and policy enforcement. As a result,
multiple ETEPs can use common keys. This works for complex mesh, hub and spoke, and multicast
networks, as well as in straightforward point-to-point topologies. Figure 1 shows ETEPs deployed in a
multipoint Ethernet network.
EncrypTight includes the following components:
● EncrypTight Element Management System (ETEMS) for appliance configuration and management
● EncrypTight Policy Manager (ETPM) for policy definition and deployment
● EncrypTight Key Management System (ETKMS) for key generation and distribution


















