UPI-C42UPI-L42
290414–14
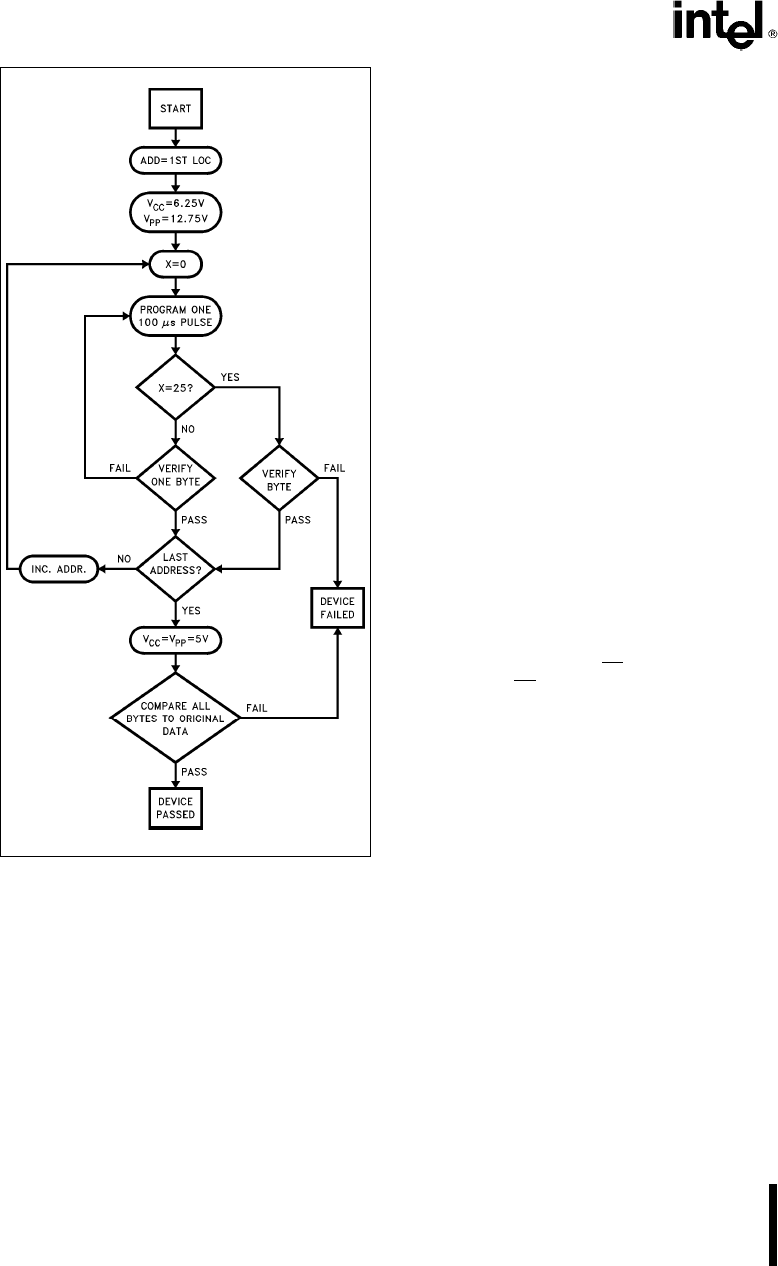
Figure 6 Quick-Pulse Programming Algorithm
Quick-Pulse Programming Algorithm
As previously stated the UPI-C42 will be pro-
grammed using the Quick-Pulse Programming Algo-
rithm developed by Intel to substantially reduce the
thorughput time in production programming
The Quick-Pulse Programming Algorithm uses initial
pulses of 100 ms followed by a byte verification to
determine when the address byte has been suc-
cessfully programmed Up to 25 100 ms pulses per
byte are provided before a failure is recognized A
flow chart of the Quick-Pulse Programming Algo-
rithm is shown in Figure 6
The entire sequence of program pulses and byte
verifications is performed at V
CC
e
625V and
V
DD
e
1275V When programming has been com-
pleted all bytes should be compared to the original
data with V
CC
e
V
DD
e
5V
A verify should be performed on the programmed
bits to ensure that they have been correctly pro-
grammed The verify is performed with T0
e
5V
V
DD
e
5V EA
e
1275V SS
e
5V PROG
e
5V
A0
e
0V and CS
e
5V
In addition to the Quick-Pulse Programming Algo-
rithm the UPI-C42 OPT is also compatible with In-
tel’s Int
e
ligent Programming Algorithm which is used
to program the NMOS UPI-42AH OTP devices
The entire sequence of program pulses and byte
verifications is performed at V
CC
e
625V and
V
DD
e
1275V When the int
e
ligent Programming
cycle has been completed all bytes should be com-
pared to the original data with V
CC
e
50 V
DD
e
5V
Verify
A verify should be performed on the programmed
bits to determine that they have been correctly pro-
grammed The verify is performed with T0
e
5V
V
DD
e
5V EA
e
1275V SS
e
5V PROG
e
5V
A0
e
0V and CS
e
5V
SECURITY BIT
The security bit is a single E PROM cell outside the
EPROM array The user can program this bit with the
appropriate access code and the normal program-
ming procedure to inhibit any external access to the
EPROM contents Thus the user’s resident program
is protected There is no direct external access to
this bit However the security byte in the signature
row has the same address and can be used to
check indirectly whether the security bit has been
programmed or not The security bit has no effect on
the signature mode so the security byte can always
be examined
SECURITY BIT PROGRAMMING
VERIFICATION
Programming
a Read the security byte of the signature mode
Make sure it is 00H
10


















