C: Networking and Security
EDS Device Servers User Guide 161
Tunneling
Tunneling provides a way to create a connection between two serial devices across an
untrusted network so the devices can share data. The sharing of information is achieved
through a direct connection (or “serial tunnel”) between the two devices that
encapsulates, authenticates, and encrypts the serial data into TCP packets and sends
them across the Ethernet network. In this way, two previously isolated and non-
networked devices can securely and effectively communicate and exchange information
and operate with existing installed software applications or devices that are configured to
run independent of an Ethernet network. And because the tunnel can be secure, anyone
who tries to monitor the conversation between the two devices would see encrypted,
unintelligible data.
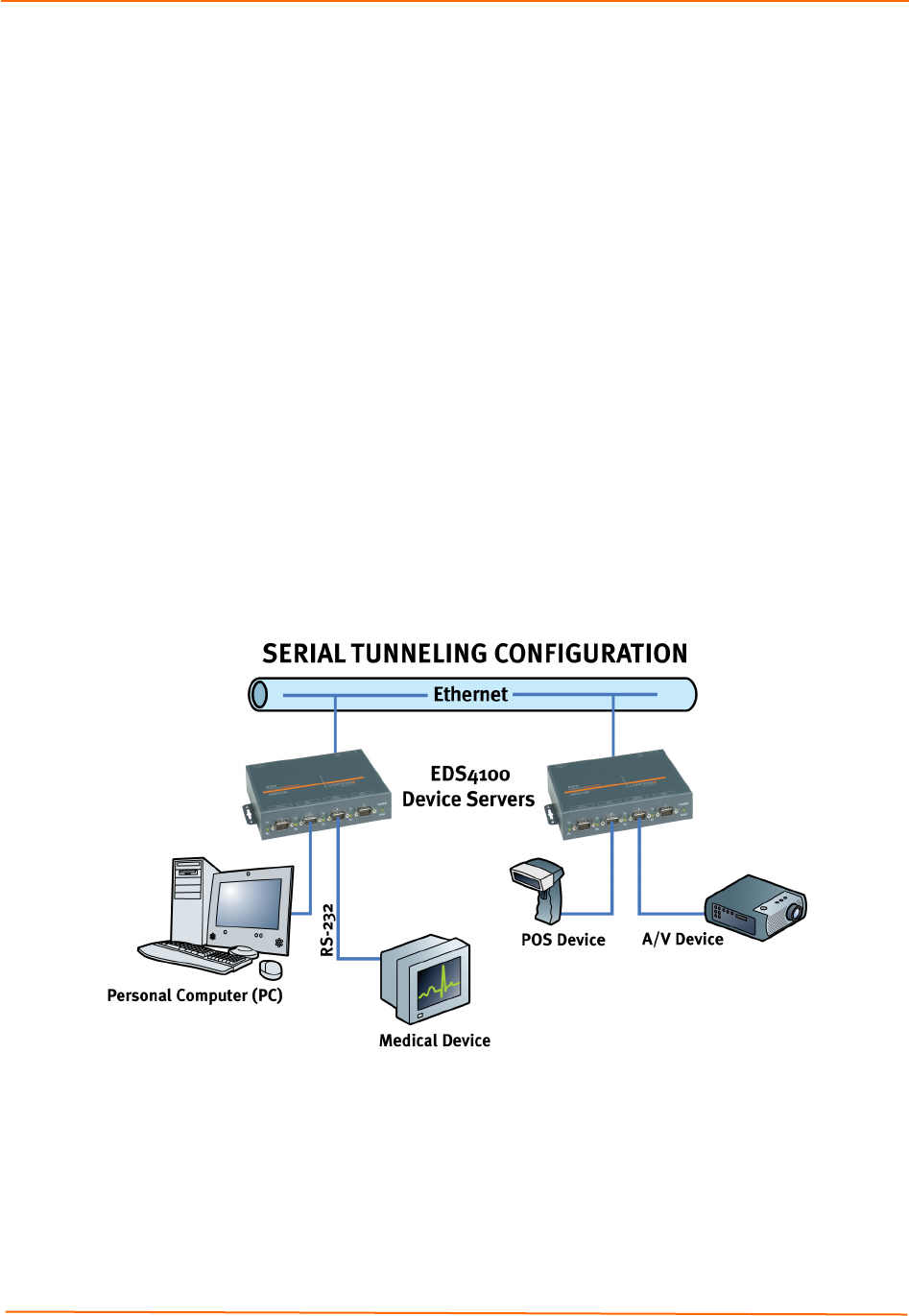
The figure below shows how a pair of device servers can be used in tandem to provide
transparent serial tunneling across an Ethernet network. In this example, a POS device in
a store collects data and sends it to a device server attached to a POS serial port. The
device server forwards the collected data, through an encrypted tunnel established over
the Ethernet network, to a device server connected to a remote PC. The data received at
the remote device server is decrypted and forwarded to the PC’s serial port and received
at the remote PC. In this way, serial data that goes in one end comes out at the other
end.
Example of an Encrypted Tunnel


















