53
Chapter 5: Setting Up and Configuring the Router
VPN Tab - Client to Gateway
10/100 8-Port VPN Router
Phase 2 SA Life Time: This field allows you to configure the length of time a VPN tunnel is active. The default
value is 3,600 seconds.
Preshared Key: Character and hexadecimal values are acceptable in this field, e.g. “My_@123” or
“4d795f40313233.” The max entry of this field is 30-digit. Both sides must use the same Pre-shared Key. It’s
recommended to change Preshared keys regularly to maximize VPN security.
Click the Save Settings button to save the settings or click the Cancel Changes button to undo the changes.
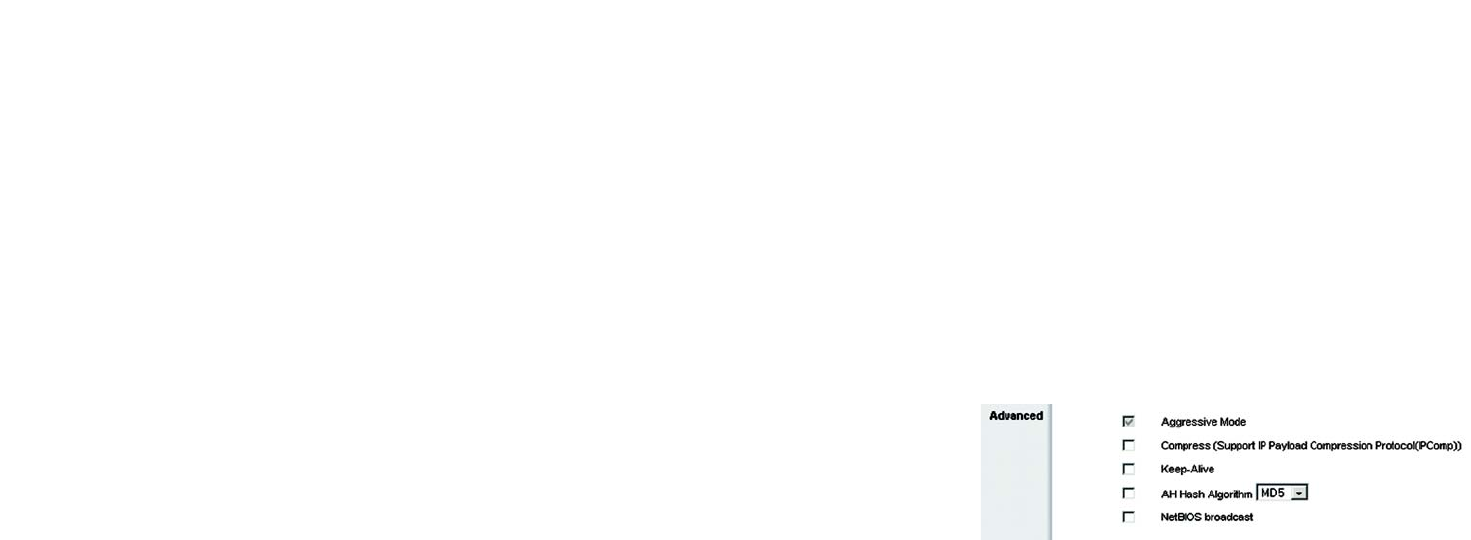
Advanced
For most users, the settings on the VPN page should be satisfactory. This device provides an advanced IPSec
setting page for some special users such as reviewers. Click the Advanced button to link you to that page.
Advanced settings are only for IKE with Preshared Key mode of IPSec.
Aggressive Mode: There are two types of Phase 1 exchanges: Main mode and Aggressive mode.
Aggressive Mode requires half of the main mode messages to be exchanged in Phase 1 of the SA exchange. If
network security is preferred, select Main mode. If network speed is preferred, select Aggressive mode. When
Group VPN is enabled, it will be limited as Aggressive Mode. If you select Dynamic IP in Remote Client Type in
tunnel mode, it will also be limited as Aggressive Mode.
Compress (Support IP Payload compression Protocol (IP Comp)
The Router supports IP Payload Compression Protocol. IP Payload Compression is a protocol to reduce the size of
IP datagrams. If Compress is enabled, the Router will propose compression when initiating a connection. If the
responders reject this propose, the Router will not implement the compression. When the Router works as a
responder, the Router will always accept compression even without enabling compression.
Keep-Alive: This mechanism helps to keep up the connection of IPSec tunnels. Whenever a connection is
dropped and detected, it will be re-established immediately.
AH Hash Algorithm: AH (Authentication Header) protocol describes the packet format and the default standards
for packet structure. With the use of AH as the security protocol, protected is extended forward into IP header to
verify the integrity of the entire packet by use of portions of the original IP header in the hashing process. There
are two algorithms, MD5 and SHA1. MD5 produces a 128-bit digest to authenticate packet data and SHA1
produces a 160-bit digest to authenticate packet data.
NetBIOS broadcast: Check the box to enable NetBIOS traffic to pass through the VPN tunnel. By default, RV082
blocks these broadcasts.
Figure 5-53: VPN tab - Client to Gateway Advanced


















