Advanced Configuration AP-700 User Guide
Alarms
83
Rogue Scan
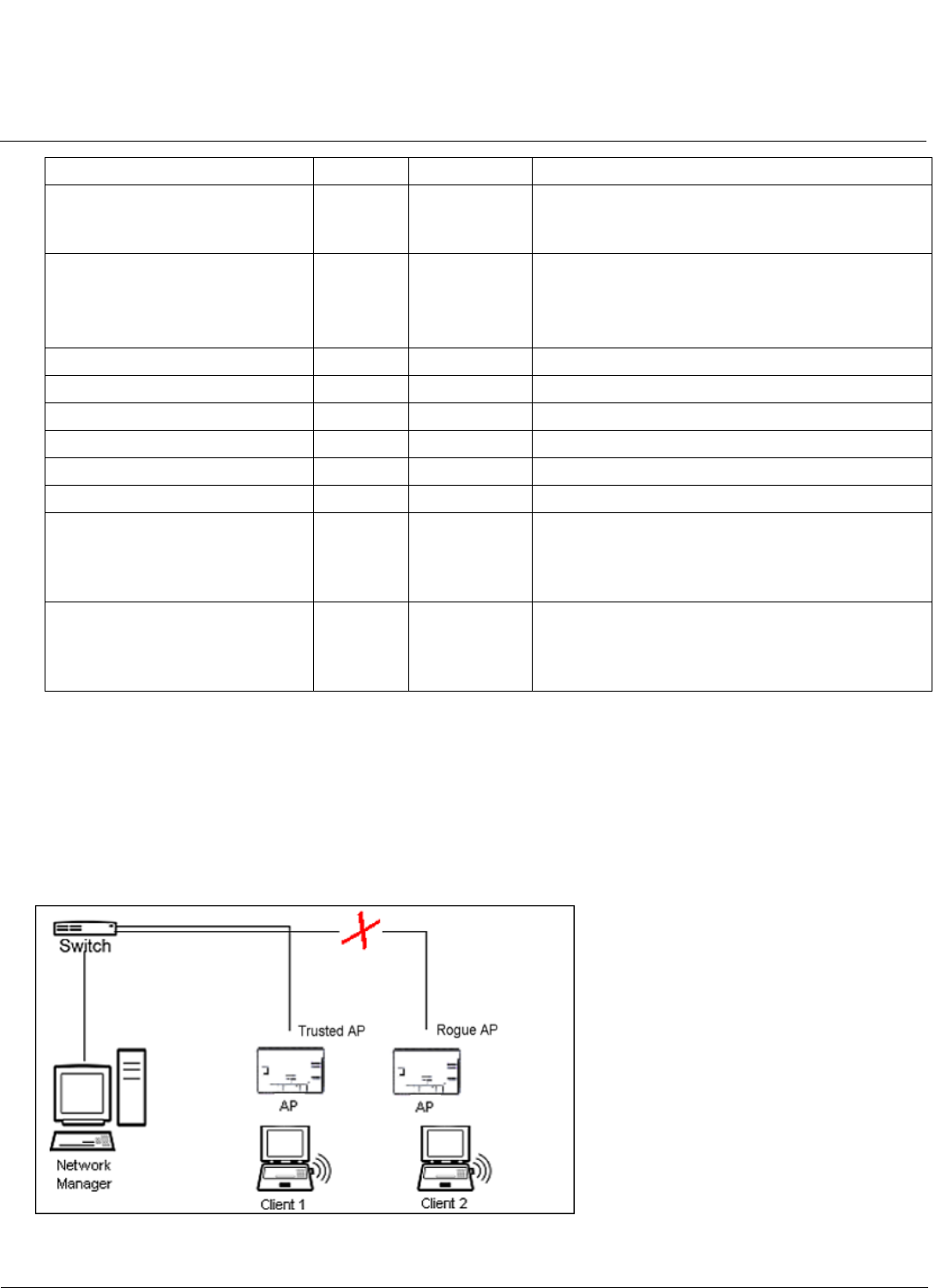
The Rogue Scan feature provides an additional security level for wireless LAN deployments. Rogue Scan uses the
selected wireless interface(s) for scanning its coverage area for Access Points and clients.
A centralized Network Manager receives MAC address information from the AP on all wireless clients detected by the AP.
The Network Manager then queries all wired switches to find out the inbound switch/port of these wireless clients. If the
switch/port does not have a valid Access Point connected to it as per a pre-configured database, the Network Manager
proceeds to block that switch/port and prevent the Rogue AP from connecting to the wired network.
Figure 4-25 Preventing Rogue AP Attacks
CLI Configuration File Execution
Errors
4 Minor There is an error in execution of the CLI
configuration file. The message specifies the
filename, line number, and error reason.
SSH Initialization Failure 3 Major One of the following failures occurs:
Keys not present
Keys cannot be generated
Internal error (no available resources)
SSH Key Generation Successful 6 Informational SSH Key generation is successful.
Wireless Service Shutdown 6 Informational Wireless service is shutdown.
Wireless Service Resume 6 Informational Wireless service resumes.
First MIC Report Attack 4 Minor First MIC report attack is detected.
Second MIC Report Attack 4 Minor Second MIC report attack is detected.
MIC Attack from Wireless Station 4 Minor A MIC attack is detected from a wireless station.
SNTP Time Retrieval Failure 4 Minor SNTP Client in the AP fails to retrieve time
information from the configured SNTP servers.
Also included in message: IP Address of SNTP
server.
SNTP Time Sync-Up Failure 4 Minor SNTP Client in the AP fails to synchronize the time
with the SNTP server it was communicating with.
Also included in message: IP Address of SNTP
server.
Syslog Message Name Priority Severity Description


















