3 – Planning
Fabric Security
3-20 59096-04 A
S
Consider the devices, switches, and management agents and evaluate the need
for authorization and authentication. Also consider whether the security database
is to distributed on the switches or centralized on a RADIUS server and how many
servers to configure.
The following examples illustrate how to configure a security database:
Security Example: Switches and HBAs with Authentication
Security Example: RADIUS Server
Security Example: Host Authentication
3.7.4.1
Security Example: Switches and HBAs with Authentication
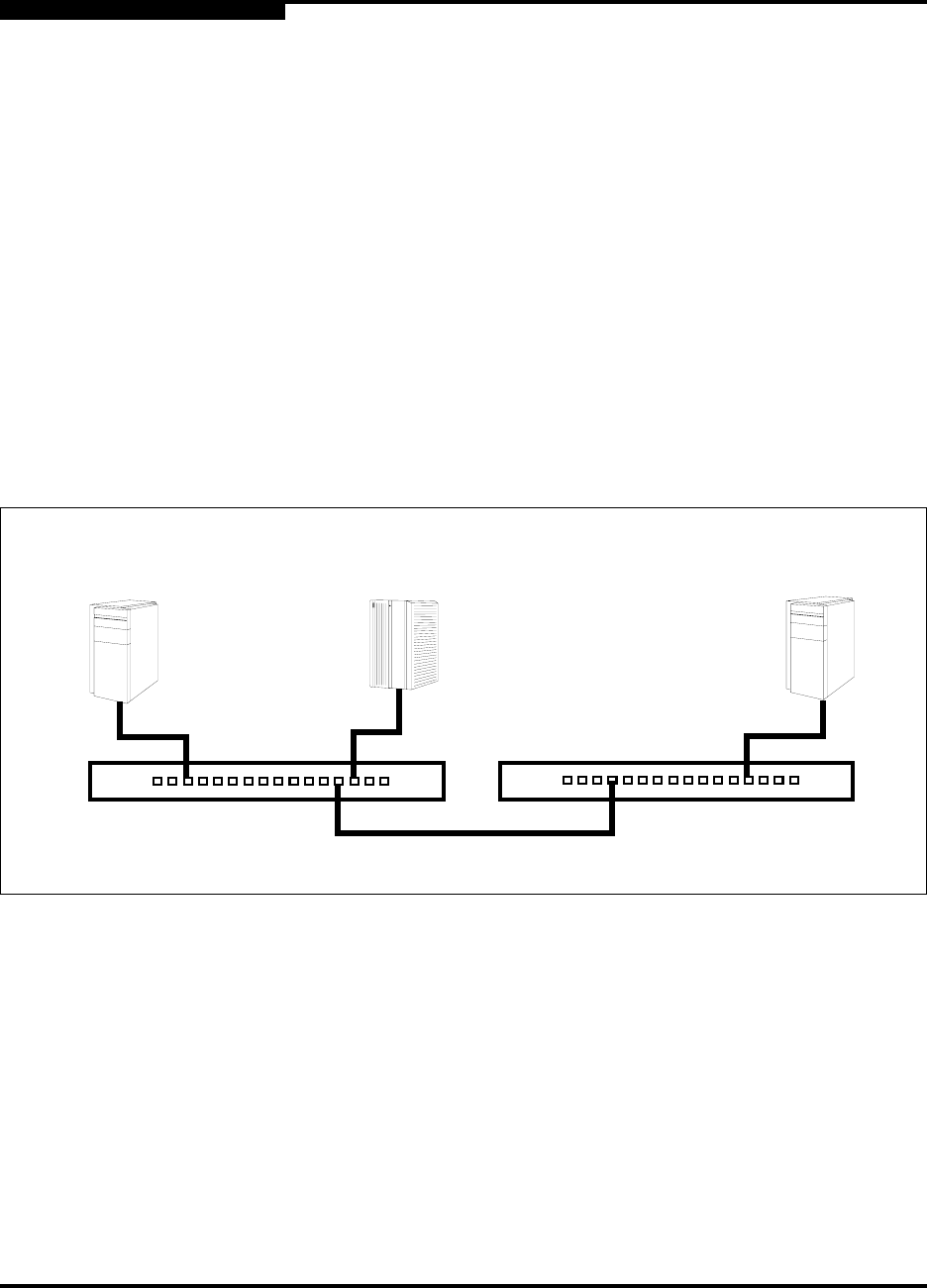
Consider the fabric shown in Figure 3-9. In this fabric, Switch_1, HBA_1, and
Switch_2 support authentication while the JBOD and HBA_2 do not. The objective
is to secure F_Ports and E_Ports in the fabric. To do this, configure security on the
devices that support security: Switch_1, Switch_2, and HBA_1.
Figure 3-9. Security Example: Switches and HBAs
Device: Switch_1
WWN: 10:00:00:c0:dd:07:e3:4c
Security: Yes
Device: Switch_2
WWN: 10:00:00:c0:dd:07:e3:4e
Security: Yes
Device: HBA_1
WWN: 10:00:00:c0:dd:07:c3:4d
Security: Yes
E_Port
F_Port
F_Port
FL_Port
Device: JBOD
WWNS:10:00:00:d1:ee:18:d4:5e
10:00:00:d1:ee:18:d4:5f
10:00:00:d1:ee:18:d4:5g
Security: No
Device: HBA_2
WWN: 10:00:00:c0:dd:07:c3:4f
Security: No


















