Prestige 650 Series User’s Guide
H-2 Log Descriptions
Chart H-2 UPnP Logs
LOG MESSAGE DESCRIPTION
UPnP pass through
Firewall
UPnP packets can pass through the firewall.
The attack logs may include the protocol (Protocol) of the packet (for example TCP or UDP) that triggered
the log.
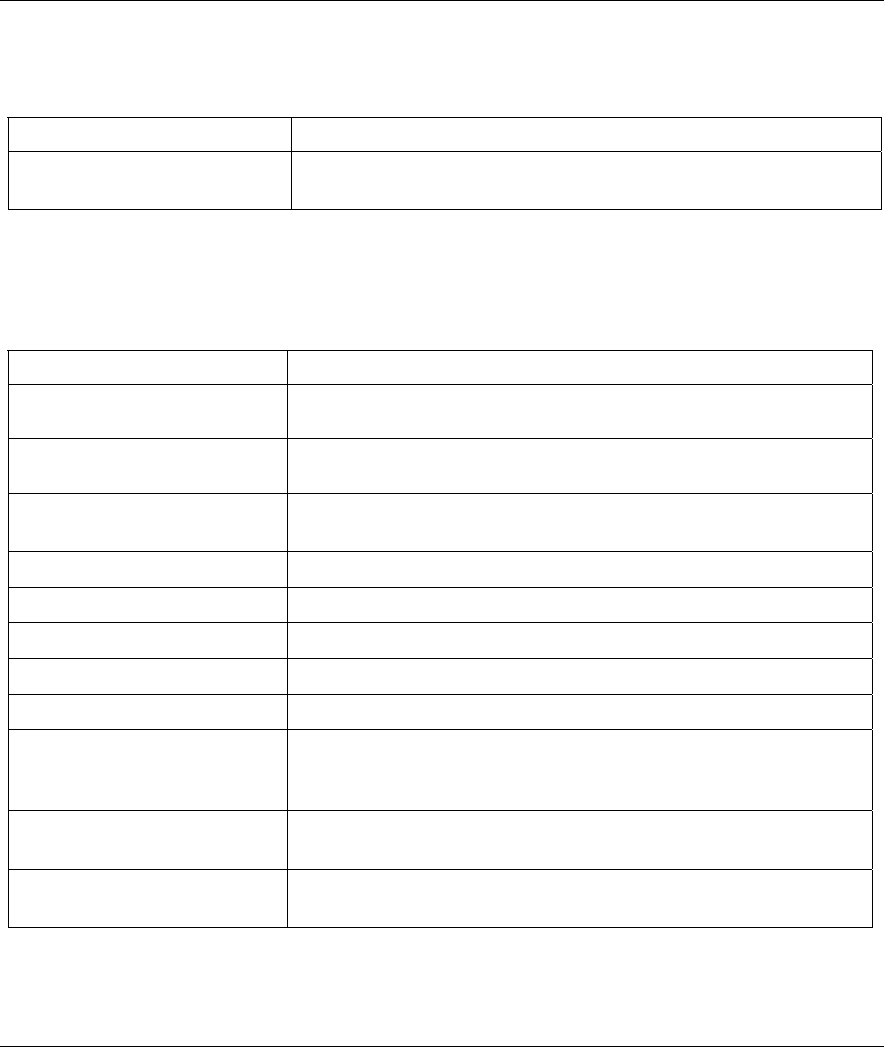
Chart H-3 Attack Logs
LOG MESSAGE DESCRIPTION
attack (Protocol)
The firewall detected an attack. The log may also display the protocol
(for example TCP or UDP).
land Protocol)
The firewall detected a land attack. The log may also display the
protocol (for example TCP or UDP).
icmp echo ICMP
(type:%d, code:%d)
The firewall detected an ICMP echo attack. See the section on ICMP
messages for type and code details.
syn flood TCP
The firewall detected a TCP syn flood attack.
ports scan TCP
The firewall detected a TCP port scan attack.
teardrop (Protocol)
The firewall detected a teardrop attack.
illegal command TCP
The firewall detected a TCP SMTP illegal command attack.
NetBIOS TCP
The firewall detected a TCP NetBIOS attack.
ip spoofing - no
routing entry
(Protocol)
The firewall detected an IP spoofing attack while the Prestige did not
have a default route. The log may also display the protocol (for
example TCP or UDP).
vulnerability ICMP
(type:%d, code:%d)
The firewall detected an ICMP vulnerability attack; see the section on
ICMP messages for type and code details.
traceroute ICMP
(type:%d, code:%d)
The firewall detected an ICMP traceroute attack; see the section on
ICMP messages for type and code details.
Access logs may include the following information: