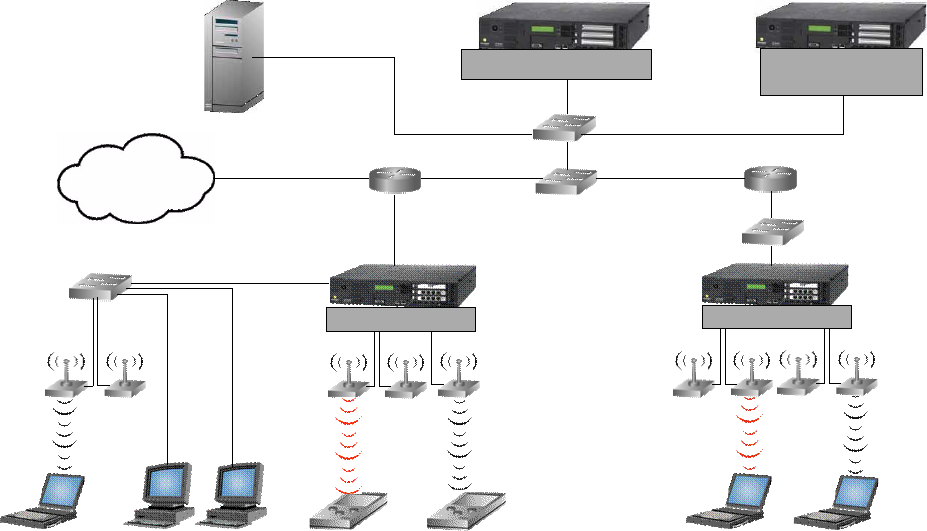
Introduction
Figure 1-1 illustrates a 700wl Series system topology that is configured with redundant Access Control
Servers for failover.
Figure 1-1. 700wl Series topology
Access Controller
Access Control Server
Access Controller
Internet
Redundant Access
Control Server
Guest Employees Untrusted User Employee Untrusted User Employee
Access Controllers sit at or near the edge of the network, and enforce authentication and access policies.
As shown in
Figure 1-1, Access Points are typically connected directly to Access Controller ports, but it is
also possible to connect APs or clients through devices such as switches or hubs. When a client is detected
at an Access Controller port, the Access Controller must first determines who the client is based on the
Authentication Policy in force for that port at that time of day. The 700wl Series system supports a variety
of authentication methods, and can interface with an organization’s existing authentication services (such
as an LDAP service, RADIUS, Kerberos, 802.1x or NT Domain Logon) or can handle authentication
through its own built-in user database.
The Access Controller actually hands off the client authentication to the central Access Control Server,
which manages the authentication process and returns the appropriate Access Policy to the Access
Controller.
An Access Policy specifies the network addresses, services, and resources the client is permitted to access.
The Access Policy can also specify that client traffic for certain destinations be redirected to alternate
destinations. This capability is used by the 700wl Series system to redirect traffic from an unknown client
to a logon page. It can also be used to notify clients when they attempt to access non-permitted resources,
or to redirect a request to a permitted resource. Traffic to a destination that is neither permitted nor
redirected is dropped. An Access Policy may also specify other settings such as bandwidth limitations,
HTTP Proxy Servers (including filtering to impose HTTP access control), and encryption requirements.
Access Policies can be configured to “expire” after a specified length of time, or at a specific time, forcing
the client to reauthenticate.
1-2 HP ProCurve Secure Access 700wl Series Management and Configuration Guide
