36
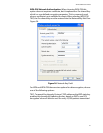
Under the Shared Key authentication, each wireless station is assumed
to have received a secret shared key over a secure channel that is
independent from the 802.11 wireless network communications
channel. To use Shared Key authentication, you must have a network
key.
WPA and WPA-PSK Authentication
Short for Wi-Fi Protected Access, a Wi-Fi standard that was designed to
improve upon the security features of WEP. The technology includes two
improvements over WEP:
❑ Improved data encryption through the temporal key integrity
protocol (TKIP). TKIP scrambles the keys using a hashing algorithm
and, by adding an integrity-checking feature, ensures that the
keys have not been tampered with.
❑ User authentication, which is generally missing in WEP, through
the extensible authentication protocol (EAP). WEP regulates
access to a wireless network based on a computer’s hardware-
specific MAC address, which is relatively simple to be sniffed out
and stolen. EAP is built on a more secure public-key encryption
system to ensure that only authorized network users can access
the network.
Data
Encryption
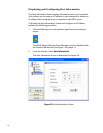
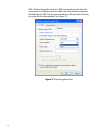
There are two protocols available for encryption: WEP and TKIP.
WEP
When you enable WEP, you can specify that a network key is used for
encryption. A network key can be provided for you automatically (for
example, it might be provided on your wireless network adapter), or you
can specify the key by typing it yourself. If you specify the key, you can
also specify the following:
❑ key length (40 bits or 104 bits)
❑ key format (ASCII characters or hexadecimal digits)
❑ key index (the location where a specific key is stored).
The longer the key length, the more secure the key. Every time the
length of a key is increased by one bit, the number of possible keys
doubles.