29-15
Cisco ASA 5500 Series Configuration Guide using the CLI
Chapter 29 Information About NAT
NAT for VPN
Figure 29-14 shows a VPN client that wants to visit a website at www.example.com. In this example, an
interface PAT rule on the outside interface matches the VPN-assigned address 10.1.1.10. With
intra-interface communication enabled, traffic can exit the same interface it entered to reach
www.example.com. A similar example without the need for hairpin networking includes an ASA for
VPN termination, and a separate ASA with NAT as the Internet gateway.
Figure 29-14 Interface PAT for Internet-Bound VPN Traffic (Hairpin, Intra-Interface)
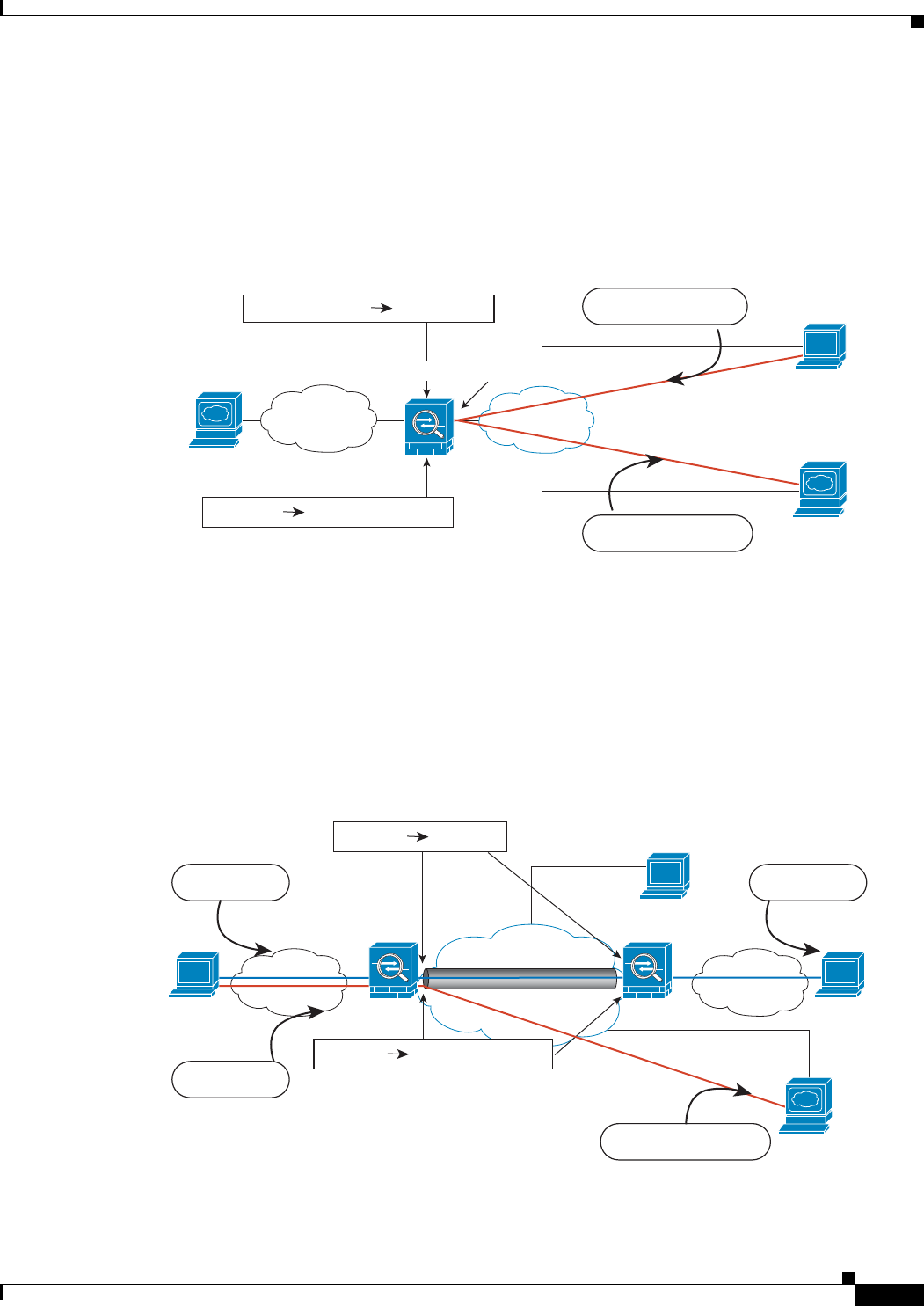
Figure 29-15 also shows an interface PAT rule for Internet-bound traffic. However, for any
communication between VPN endpoints such as the ends of a site-to-site tunnel, you do not want to
perform NAT. Therefore you also need to create an identity NAT rule (using twice NAT) for any traffic
that goes to other inside networks connected by VPN.
Figure 29-15 Identity NAT to Allow Communication Between VPN Sites and Clients
VPN Client
209.165.201.10
Internet
Src: 209.165.201.10
10.1.1.10
203.0.113.1:6070
10.1.1.10
Inside Server
www.example.com
Inside
209.165.201.10
1. HTTP request to www.example.com
4. HTTP request to www.example.com
2. ASA replaces src address with local address
3. ASA performs interface PAT for outgoing traffic.
Note: This “hairpin” traffic flow requires you to enable
intra-interface communication.
Src: 203.0.113.1:6070
ASA Outside IP: 203.0.113.1
331396
San Jose VPN Client
VPN IP: 10.3.3.2
10.1.1.6
ASA ASA
10.2.2.78
Internet
Src: 10.1.1.6
10.1.1.6
203.0.113.1:6070
10.1.1.6 10.1.1.6
www.example.com
San Jose
Boulder
1. IM to 10.2.2.78
Src: 10.1.1.6
A. HTTP to
www.example.com
Src: 10.1.1.6
3. IM received
C. HTTP request to www.example.com
2. Identity NAT for 10.1.1.0, 10.2.2.0, & 10.3.3.0
networks when going to other inside networks
connected by VPN
B. ASA performs interface PAT for
outgoing traffic. Note: For remote access
VPN Clients, this “hairpin” traffic flow
requires you to enable
intra-interface communication.
Src: 203.0.113.1:6070
Site-to-Site VPN Tunnel
331395


















