Configuration and Management
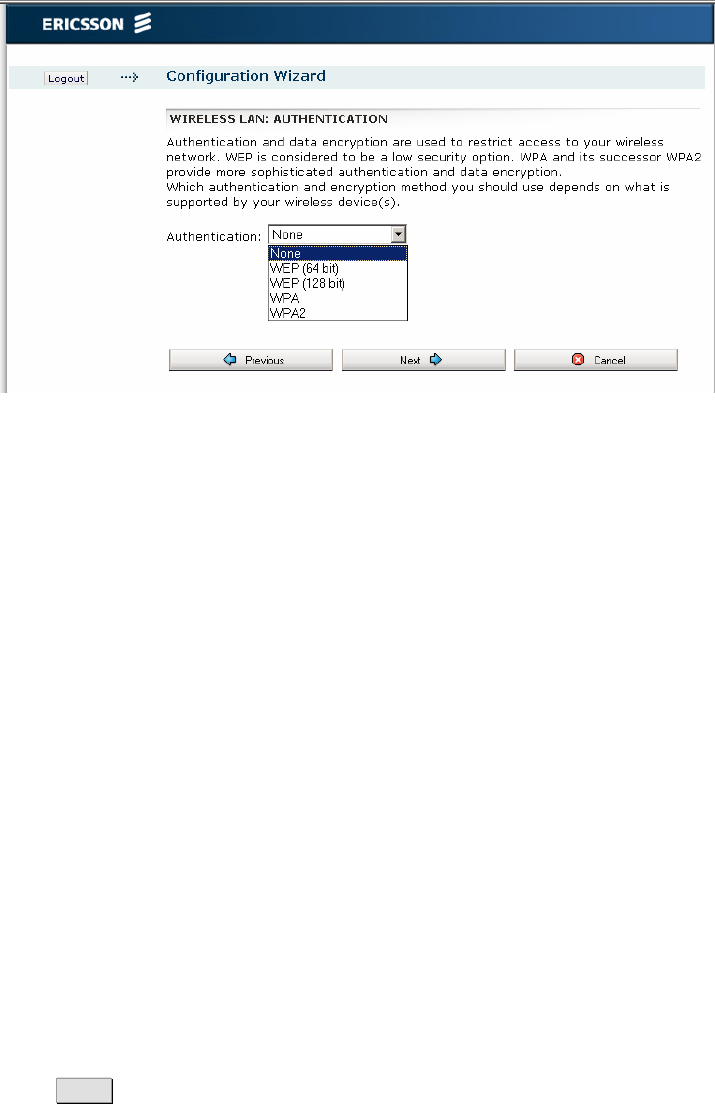
Figure 16 – Wireless LAN: Authentication page
Select one of the authentication methods from the “Authentication” drop-
down list. The available options are as follows:
• None;
f you select “None” as authentication method no client configuration is
needed but be aware of that the WLAN will now be open without any
kind of security.
• WEP (64 bit), WEP (128 bit);
WEP (Wired Equivalent Privacy) is considered to be a low security
option. WEP encrypted data is translated into blocks of either 64 bits
length or 128 bits length.
• WPA, WPA2;
WPA (Wi-Fi Protected Access) and its successor WPA2 are the most
reliable security options. WPA encryption uses the Temporal Key
Integrity Protocol (TKIP) while WPA2 encryption follows the Advanced
Encryption Standard (AES). AES offers a higher level of security and is
approved for sensitive corporate and government data transmission.
Note: Make sure that the operating system(s) and Wireless LAN
interface(s) of the wireless client(s) support the selected
authentication method.
Click Next to proceed.
5/1551-CRH 102 167 Uen Rev E 2008-02-15
23


















