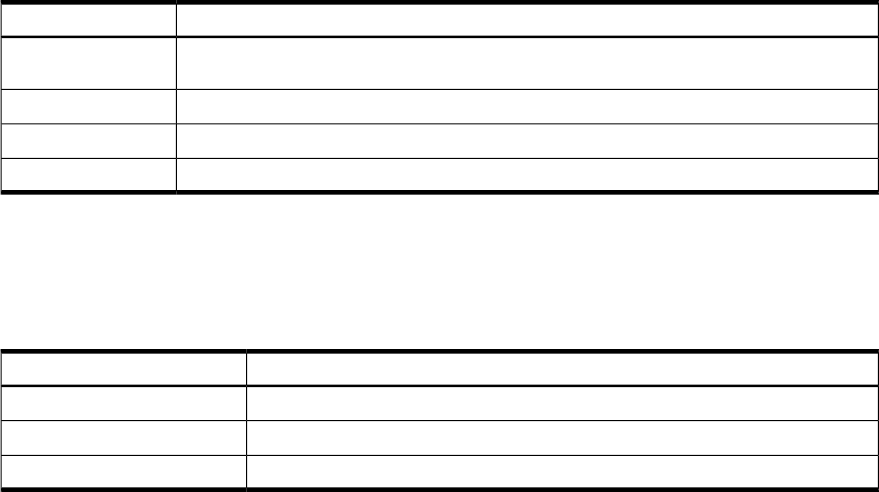
Table 6-2 Minor Numbers for sctl Device Files
ConstructionMinor Number
Two hexadecimal digits, identifying the controlling interface card by its instance number. The
instance value is displayed in ioscan output, under column I for the interface hardware type.
CC
One hexadecimal digit identifying the drive (target) address.T
One hexadecimal digit identifying the LUN within the deviceL
Hexadecimal digit zero, for reserved portion of the minor number.0
The following is an example of the tape device:
# /usr/sbin/mknod /dev/rscsi/c6t5d0 c 203 0x065002
5. Use the located or created sctl device file in specifying the attached device.
Use this resource statementFor this attached device
tape:scsi::attach:/dev/rscsi/c6t5d0
Tape
changer:scsi::attach:/dev/rscsi/c6t0d0
Media changer
burner:scsi::attach:/dev/rscsi/c4t3d0
CD/DVD burner
Attached devices cannot be shared simultaneously across active virtual machines. Only one active virtual
machine can be given a particular attacheddevice at a time. However, like virtualdevices, attached devices
can be attachedand detached dynamicallyacross active virtualmachines (see “Using IntegrityVM Storage”
(page 82)). Also, as the device is being attached to a virtual machine, it cannot be opened by the VM Host
at the time of or during attachment.
Because tapes, media changers, and CD/DVD burners are not virtualized, media changes with them must
be done physically. Therefore, all media changes with attached devices must be done by individuals with
access to that physical storage. Changes to attached devices may require the device to be unlocked from
an active guest OS. Attached devices remain in the last lock state the guest OS put it in when the device
is detached or the virtual machine is shut down. Empty devices are attached and are not locked.
No multipath solutions are available for attached devices on the VM Host. No multipath products are
supported in the virtual machine.
Manage attached devices to prevent the wrong virtual machines from viewing sensitive information. You
can displaywhich virtual machines arecurrently using attached devicesusing the hpvmstatus command.
6.3 Using Integrity VM Storage
The following sections describe the roles of individuals accessing virtual storage, the commands they use,
and some examples of using Integrity VM storage.
6.3.1 Integrity VM Storage Roles
This section describes the roles that individuals play in working with Integrity VM storage. Each role has
different responsibilities inusing Integrity VM storage. Theroles may be played by one ormore individuals
depending on security requirements and skill sets. The three roles are:
• “VM Host Administrator” (page 82)
• “Guest Administrator” (page 83)
• “Guest User” (page 83)
6.3.1.1 VM Host Administrator
The VM Hostadministrator role is an individualresponsible for the proper configurationand maintenance
of the VM Host for running virtual machines. As such, this person needs complete access to the VM Host
to install hardware and software. This person also needs to understand how to do HP-UX system
maintenance, howto configure hardware properly, andhow to set upand use various software applications
and tools.
82 Creating Virtual Storage Devices


















