26 DOMINION KX II USER GUIDE
Authentication vs. Authorization
Authentication is the process of verifying that a user is who he says he is. Once a user is
authenticated, the user’s group is used to determine his system and port permissions. The user’s
assigned privileges determine what type of access is allowed. This is called authorization.
When Dominion KX II is configured for remote authentication, the external authentication server
is used primarily for the purposes of authentication, not authorization.
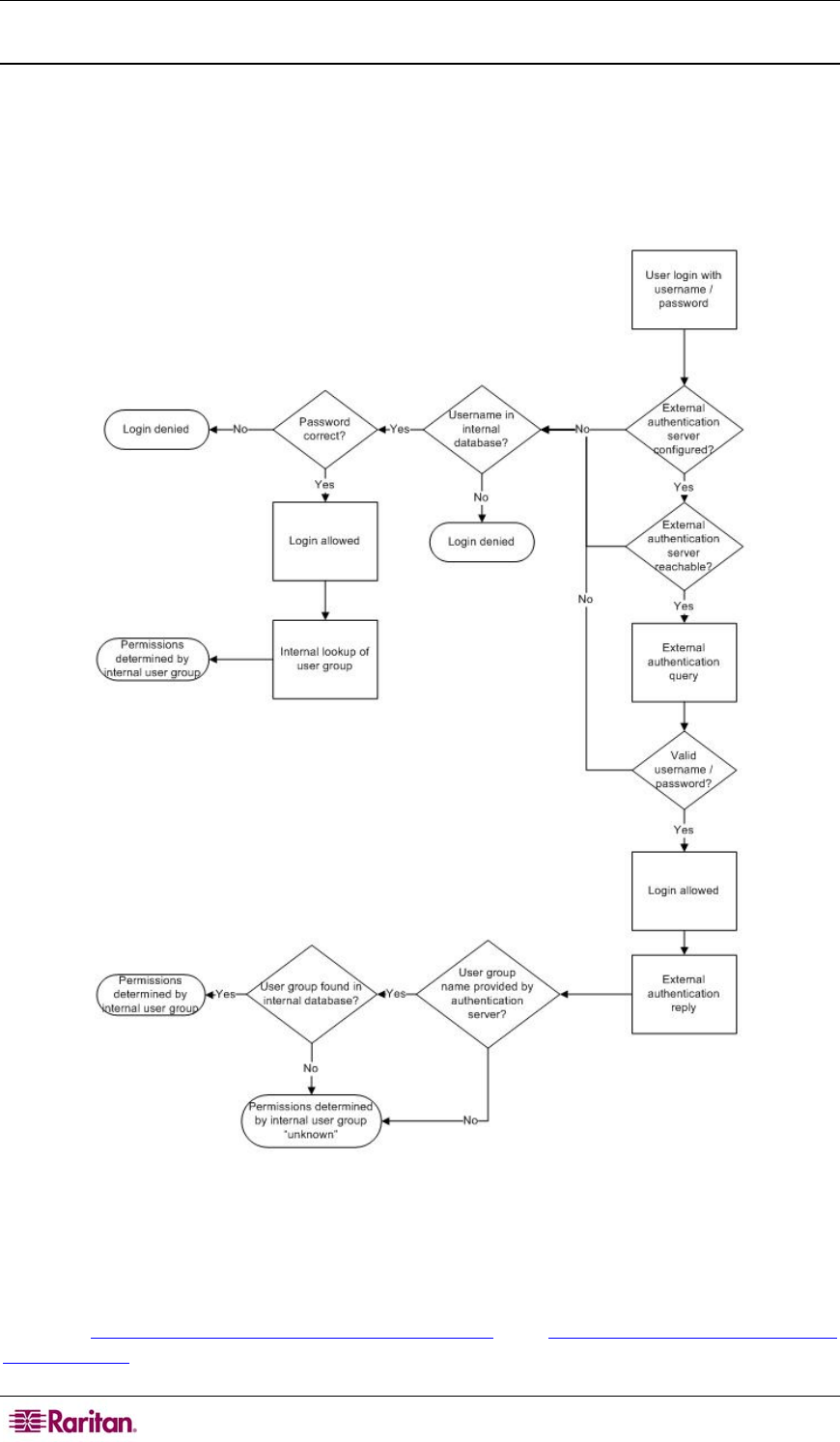
The flow diagram illustrates this process:
Figure 10: Authentication/Authorization Flow Diagram
Note the importance of the group to which a given user belongs, as well as the need to configure
the group named, “Unknown”. If the external authentication server returns a group name that is
not recognized by the Dominion KX II, that user’s permissions are determined by the permanent
group named “Unknown”.
Refer to Implementing LDAP Remote Authentication
and Implementing RADIUS Remote
Authentication to determine how to configure your authentication server to return user group
information to the Dominion KX II as part of its reply to an authentication query.


















