37-4
Cisco ASA 5500 Series Configuration Guide using ASDM
Chapter 37 Configuring Access Rules
Information About Access Rules
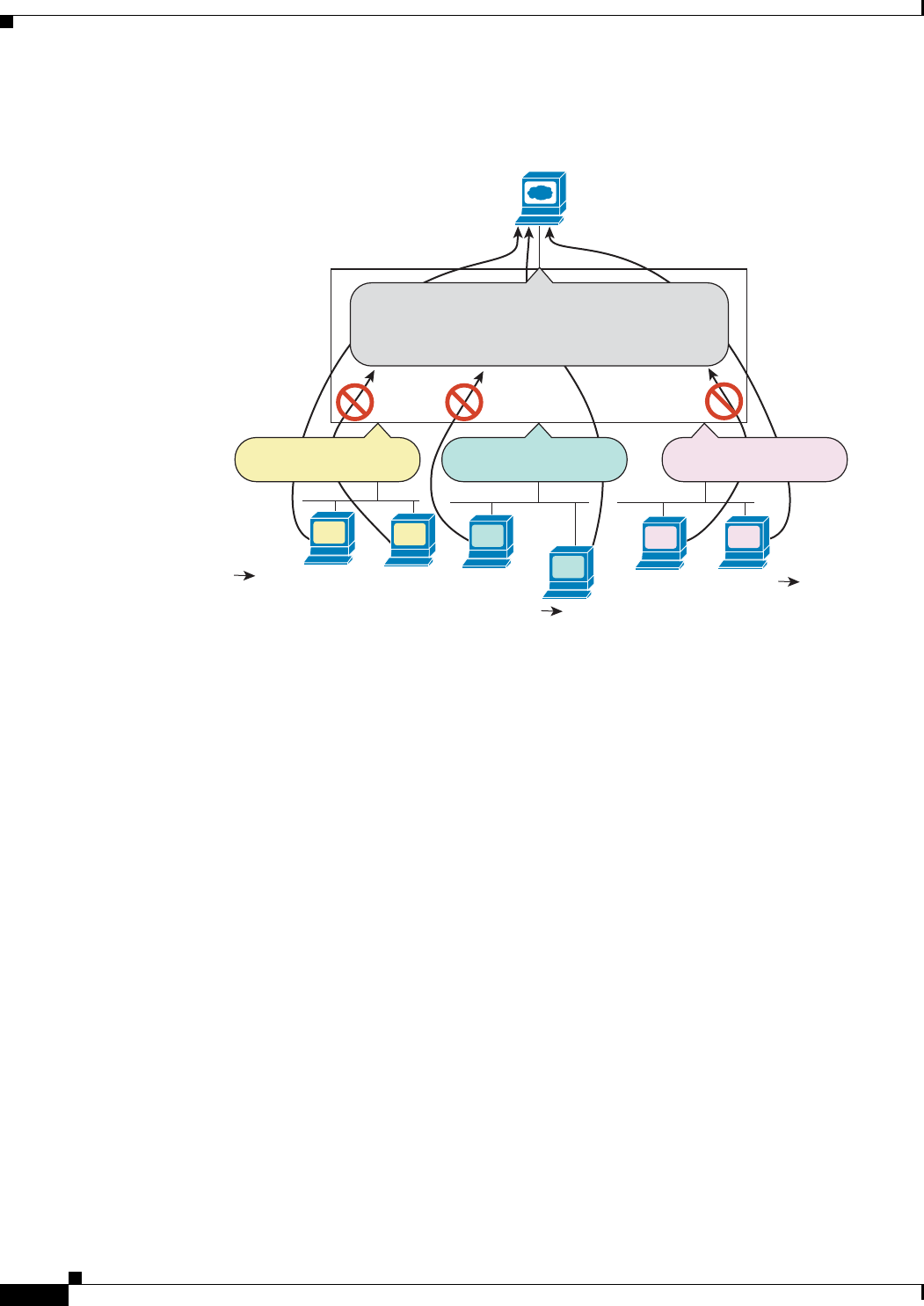
Figure 37-1 Outbound Access List
Information About Access Rules
This section describes information about access rules and includes the following topics:
• Access Rules for Returning Traffic, page 37-4
• Allowing Broadcast and Multicast Traffic through the Transparent Firewall Using Access Rules,
page 37-5
• Management Access Rules, page 37-5
Access Rules for Returning Traffic
For TCP and UDP connections for both routed and transparent mode, you do not need an access rule to
allow returning traffic because the ASA allows all returning traffic for established, bidirectional
connections.
For connectionless protocols such as ICMP, however, the ASA establishes unidirectional sessions, so
you either need access rules to allow ICMP in both directions (by applying access lists to the source and
destination interfaces), or you need to enable the ICMP inspection engine. The ICMP inspection engine
treats ICMP sessions as bidirectional connections.
Web Server:
209.165.200.225
Inside
HR
Eng
Outside
Static NAT
209.165.201.410.1.1.14
Static NAT
209.165.201.610.1.2.67
Static NAT
209.165.201.810.1.3.34
ACL Outbound
Permit HTTP from 10.1.1.14, 10.1.2.67,
and 10.1.3.34 to 209.165.200.225
Deny all others
ACL Inbound
Permit from any to any
ACL Inbound
Permit from any to any
ACL Inbound
Permit from any to any
ASA
333823


















