Vigor3300 Series User’s Guide
83
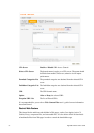
Enable Block IP Options Activates the Block IP options function. The router will ignore
any IP packets with IP option field appearing in the datagram
header.
Enable Block Land Activates the Block Land function. A Land attack occurs when
an attacker sends spoofed SYN packets with
identical source address, destination addresses and port number
as those of the victim.
Enable Block Smurf Activates the Block Smurf function. The router will reject any
ICMP echo request destined for the broadcast address.
Enable Block Trace Route Activates the Block trace route function. The router will not
forward any trace route packets.
Enable Block SYN
Fragment
Activates the Block SYN fragment function. Any packets
having the SYN flag and fragmented bit sets will be dropped.
Enable Block Fraggle
Attack
Activates the Block fraggle Attack function. Any broadcast
UDP packets received from the Internet are blocked.
Enable TCP Flag Scan Activates the Block TCP flag scan function. Any TCP packet
with an anomalous flag setting is dropped. These scanning
activities include no flag scan, FIN without ACK scan, SYN
FIN scan, Xmas scan and full Xmas scan.
Enable Tear Drop Activates the Block Tear Drop function. This attack involves
the perpetrator sending overlapping packets to the target hosts
so that target host will hang once they re-construct the packets.
The routers will block any packets resembling this attacking
activity.
Enable Ping of Death Activates the Block Ping of Death function. Many machines
may crash when receiving an ICMP datagram that exceeds the
maximum length. The router will block any fragmented ICMP
packets with a length greater than 1024 octets.
Enable Block ICMP
Fragment
Activates the Block ICMP fragment function. Any ICMP
packets with fragmented bit sets are dropped.
Enable Block Unknown
Protocol
Activates the Block Unknown Protocol function. The router
will block any packets with unknown protocol types.
Click Apply to apply the settings when you finish the configuration.
3
3
.
.
4
4
.
.
3
3
U
U
R
R
L
L
F
F
i
i
l
l
t
t
e
e
r
r
The Internet contains a wide range of offenses or illegal materials. Unlike traditional media,
the Internet does not have any obvious tools to segregate materials based on URL strings or
content. URL content filtering systems are seen as tools that would provide the cyberspace
equivalent of the physical separations that are used to limit access to particular materials. By