AirborneDirect™ Users Guide Quatech, Inc.
100-8510-110 2/21/2011 71
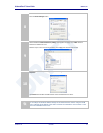
20.3 Configuring Serial Port 2 for Access on Tunnel Port
A data tunnel can be made using the devices tunnel port as the network
connection port. This does not require authenticating with the device and
automatically initiates the tunnel connection. Configuring the device to support
this approach to establishing a data tunnel is covered in the following table.
Table 38 – Configure Data Tunnel on Serial Port 2 Tunnel Port (TCP)
Step
Description
Navigation Bar
Select Configuration
You will see a group of fields under the banner
of WLAN Parameters.
Feature Link
Select Connection Settings
The wireless interface and security must be
configured before configuring the Ethernet
settings.
A page showing the configuration options for
TCP/IP and UDP connections to the device.
Configuration of Telnet, HTTP and SSH ports is
possible through this page.
Select Tunnel Enabled – Serial Port 2
Select Enabled.
Select Tunnel Port – Serial Port 2
Enter the port to be used for the tunnel.
Default is 8024, this should only be changed if
a port is already defined for the application
server or it is already being used by another
service.
Select Tunnel Mode – Serial Port 2
Select TCP from drop down menu.
Press Commit [Button]
Saves changes to the device.
Press Reload [Button]
Reloads the Connection Settings page.
Feature Link
Select Serial Port 2 Settings
The wireless interface and security must be
configured before configuring the Ethernet
settings.
Displays a page showing the serial port
configuration, setting the default mode of
operation for the serial interface is done in this
page.
Select Serial CLI Default Mode
Select Listen from the drop down menu.
Press Commit [Button]
Saves changes to the device.
Optional
Press Reload [Button]
Reloads the Serial Port 2 Settings page.
Select this is you have further configuration
options to change.
Optional
Press Restart [Button]
Restarts the device. After the device as
rebooted it will attempt to authenticate to the
configured network. As long as the network is
in range the wireless interface will connect.
Once authenticated the network it is possible
for a TCP/IP connection to be made on the
Telnet port.
To establish a data tunnel and gain access to the serial data from the WLAN or
Ethernet interface follow the steps in Table 39.