48
Chapter 7: Setting up the Wireless-G Router for Broadband WAN and Mobile Broadband Ser-
vice
Wireless-G Router for Mobile Broadband
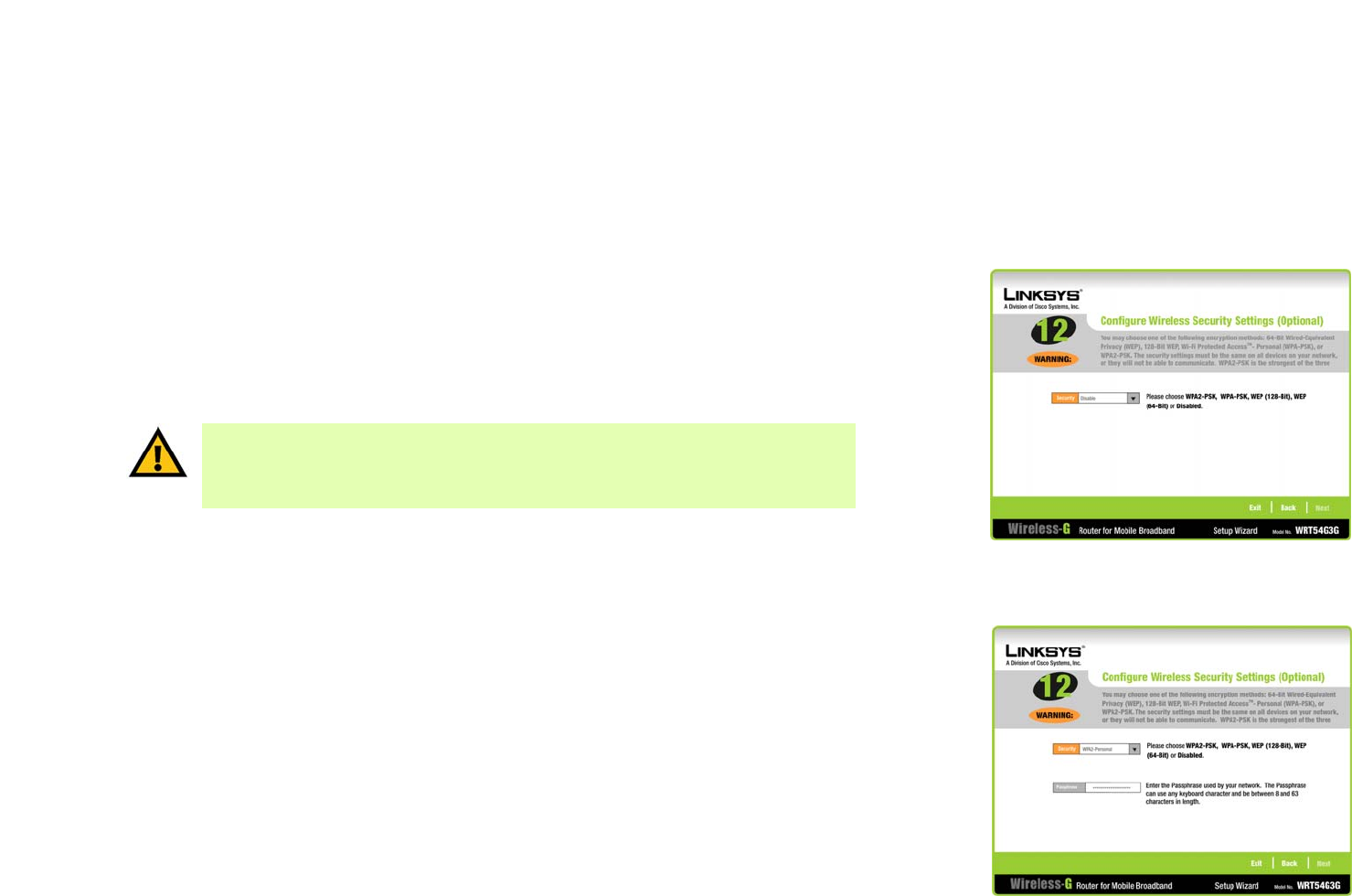
15. Select the method of security you want to use: WPA2-PSK, WPA-PSK, WEP (128-Bit), or WEP (64-Bit). WPA
stands for Wi-Fi Protected Access, and WEP stands for Wired Equivalent Privacy. WPA is a stronger security
method than WEP. WPA2 is the strongest security method. Proceed to the appropriate section for your security
method.
If you want to use WPA-Enterprise (also called WPA-RADIUS), WPA2-Enterprise, or RADIUS, then you should
select Disabled and use the Router’s Web-based Utility to configure your wireless security settings. Click the
Next button. You will see a warning message that recommends that you enable wireless security on your
wireless network. Click the Exit button and proceed to step 18.
If you do not want to use any wireless security method, select Disabled and then click the Next button.You
will see a warning message that recommends that you enable wireless security on your wireless network.
WPA2-Personal
To use WPA2-PSK security, enter a Passphrase that is 8-32 characters in length.
Passphrase - Enter a passphrase, also called a pre-shared key, of 8-63 characters in the Passphrase field.
The longer and more complex your Passphrase is, the more secure your network will be.
Click the Next button to continue or the Back button to return to the previous screen.
wpa (wi-fi protected access: a wireless security protocol
using TKIP (Temporal Key Integrity Protocol) encryption,
which can be used in conjunction with a RADIUS server.
encryption: encoding data transmitted in a network.
wep (wired equivalent privacy): a method of encrypting network
data transmitted on a wireless network for greater security.
IMPORTANT: Linksys strongly recommends that you enable wireless security on your
wireless network. Otherwise, unauthorized users may be able to access the Internet using
your service and incur additional charges. You are liable for any and all additional charges
from your service provider.
Figure 7-16: Configure Wireless Security
Settings Screen
Figure 7-17: Configure Wireless Security
Settings - WPA2-PSK Screen
wpa2 (wi-fi protected access2: a wireless security protocol
using TKIP (Temporal Key Integrity Protocol) encryption and
AES (Advanced Encryption System) with dynamic encryption
keys, which can be used in conjunction with a RADIUS server.


















