Device Security 107
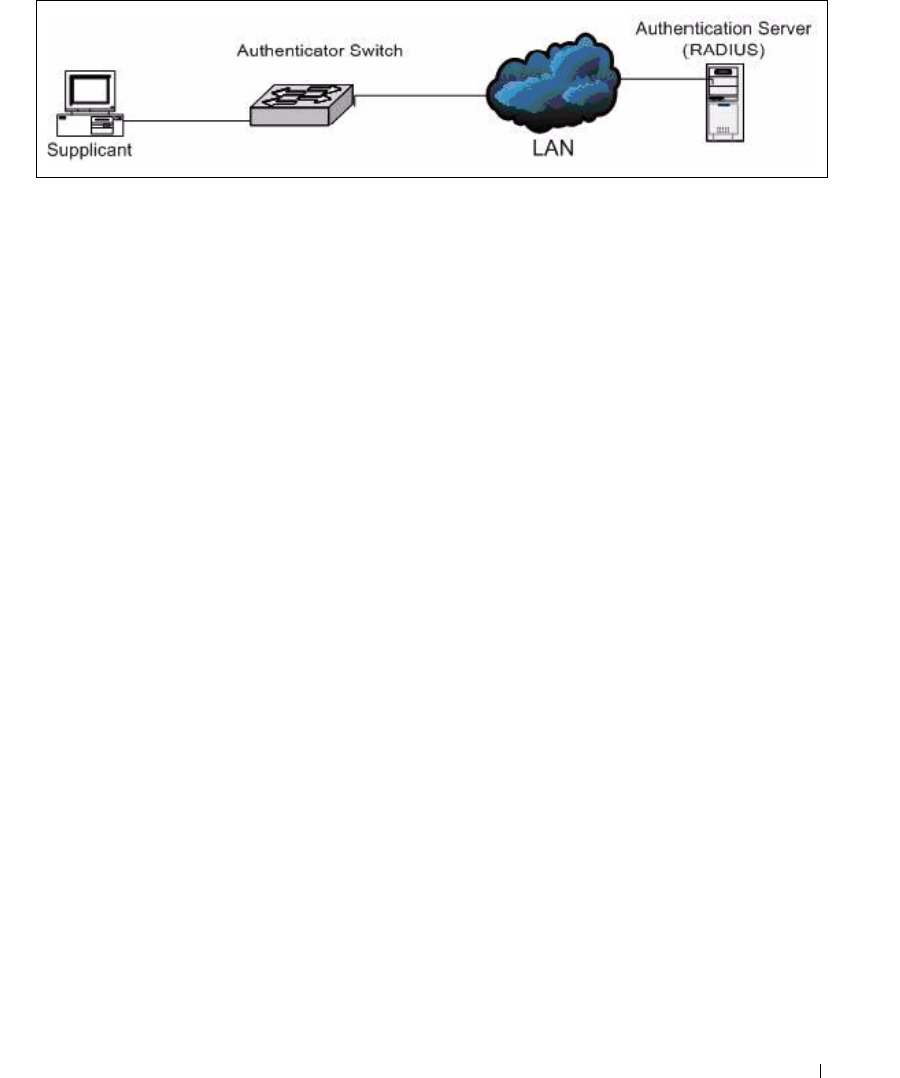
Figure 5-1. Switch with 802.1x Network Access Control
If a user, or supplicant, attempts to communicate via the switch on any interface except interface 1/g1,
the system challenges the supplicant for login credentials. The system encrypts the provided information
and transmits it to the RADIUS server. If the RADIUS server grants access, the system sets the 802.1x
port state of the interface to authorized and the supplicant is able to access network resources.
console(config)#radius-server host 10.10.10.10
console(Config-radius)#exit
console(config)#radius-server key secret
console(config)#exit
console#show radius-servers
IP address Type Port TimeOut Retran. DeadTime Source IP Prio. Usage
------------- ----- ----- ------- ------- -------- ------------- ----- -----
10.27.5.157 Auth 1812 Global Global Global 10.27.65.13 0 all
Global values
Configured Authentication Servers : 1
Configured Accounting Servers : 0
Named Authentication Server Groups : 1
Named Accounting Server Groups : 0
Timeout : 3
Retransmit : 3
Deadtime : 0
Source IP : 0.0.0.0
RADIUS Attribute 4 Mode : Disable
RADIUS Attribute 4 Value : 0.0.0.0
console(config)#aaa authentication login radiusList radius
console(config)#aaa authentication dot1x default radius
console(config)#dot1x system-auth-control
console(config)#interface ethernet 1/g1
console(config-if-1/g1)#dot1x port-control force-authorized
console(config-if-1/g1)#exit


















