Device Security 123
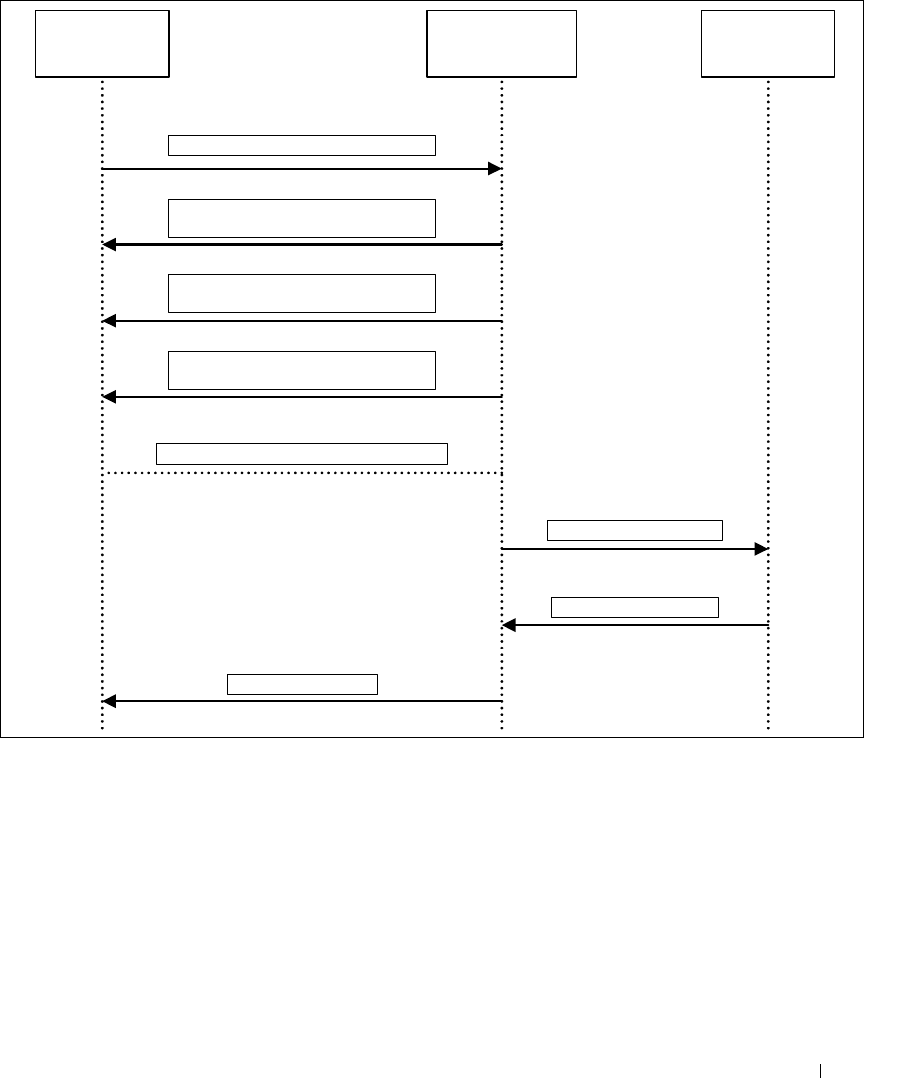
Figure 5-5. MAB Operation – Authentications Based on MAC Address in Database
CLI Examples
Example 1: Enable/Disable MAB
To enable/disable MAB on interface 1/5, use the following commands:
console(config-if-1/g5)#dot1x mac-auth-bypass
console(config-if-1/g5)#no dot1x mac-auth-bypass
Client DOT 1x/MAB RADIUS
Traffic from unknown client, Learn MAC
EAPOL Timeout – Initiate MAB (30 seconds)
EAPOL Request (Identity)
D=01.80.c2.00.00.03 (30 seconds)
RADIUS Access-Accept
RADIUS Access-Request
Client Authentication
EAPOL Request (Identity)
D=01.80.c2.00.00.03 (30 seconds)
EAPOL Request (Identity)
D=01.80.c2.00.00.03


















