Utility 173
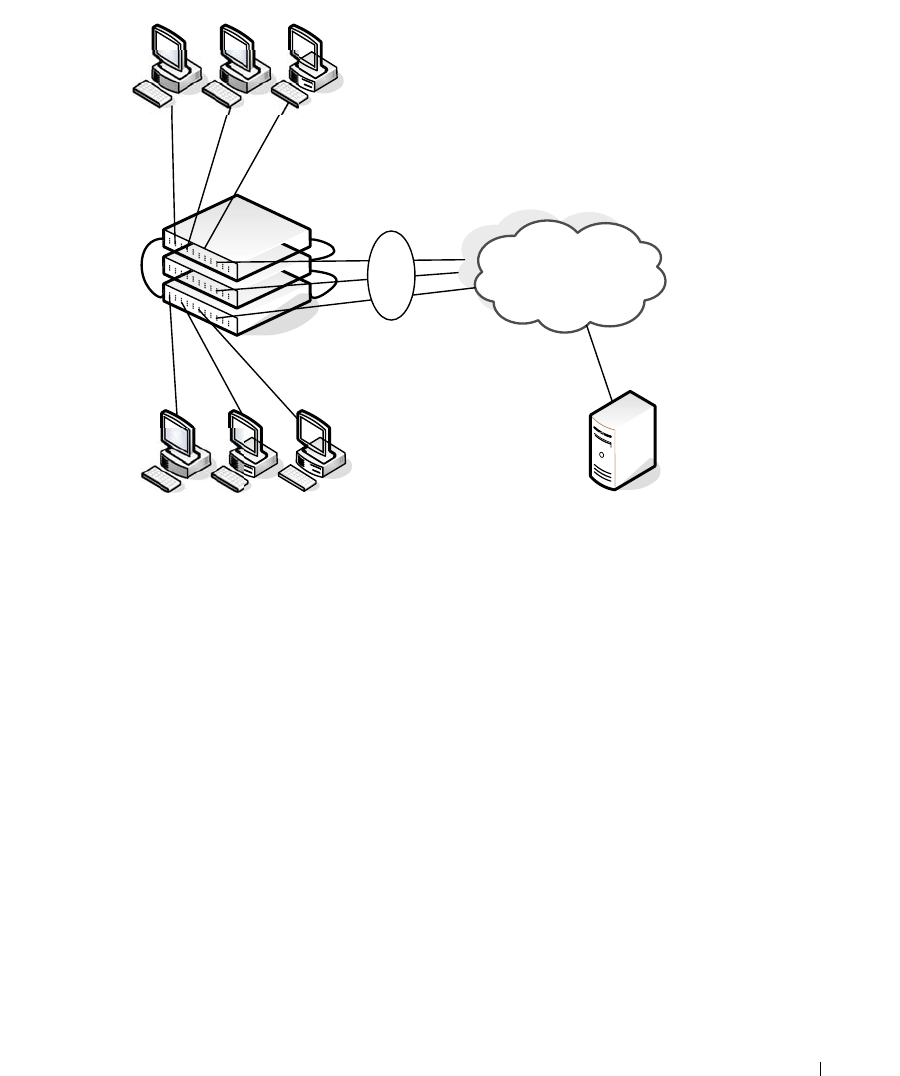
Figure 9-3. NSF and DHCP Snooping
If the management unit fails, all hosts connected to that unit lose network access until that unit reboots.
The hardware on surviving units continues to enforce source filters IPSG installed prior to the failover.
Valid hosts continue to communicate normally. During the failover, the hardware continues to drop data
packets from unauthorized hosts so that security is not compromised.
If a host is in the middle of an exchange with the DHCP server when the failover occurs, the exchange is
interrupted while the control plane restarts. When DHCP snooping is enabled, the hardware traps all
DHCP packets to the CPU. The control plane drops these packets during the restart. The DHCP client
and server retransmit their DHCP messages until the control plane has resumed operation and messages
get through. Thus, DHCP snooping does not miss any new bindings during a failover.
As DHCP snooping applies its checkpointed DHCP bindings, IPSG confirms the existence of the
bindings with the hardware by reinstalling its source IP address filters.
If Dynamic ARP Inspection is enabled on the access switch, the hardware traps ARP packets to the CPU
on untrusted ports. During a restart, the control plane drops ARP packets. Thus, new traffic sessions may
be briefly delayed until after the control plane restarts.
If IPSG is enabled and a DHCP binding is not checkpointed to the backup unit before the failover, that
host will not be able to send data packets until it renews its IP address lease with the DHCP server.
DHCP Server
LAG
`
` `
` `
Hosts
Hosts