DG834N RangeMax NEXT Wireless ADSL2+ Modem Router Reference Manual
3-8 Protecting Your Network
v1.0, October 2008
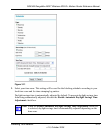
This screen allows you to configure the following settings:
• Service. From this list, select the application or service to be allowed or blocked. The list
already displays many common services, but you are not limited to these choices. Use the
Services screen to add any additional services or applications that do not already appear. See
“How to Define Services” on page 3-13.
• Action. Choose how you want this type of traffic to be handled. You can block or allow
always, or you can block or allow according to the schedule you have defined in the Services
screen:
– ALLOW always. Traffic for the selected service is always allowed.
– ALLOW by schedule, otherwise Block. Traffic for the selected service is allowed
according to how the service is defined in the Services screen, but otherwise blocked.
– BLOCK always. Traffic for the selected service is always blocked.
– BLOCK by schedule, otherwise Allow. Traffic for the selected service is blocked
according to how the service is defined in the Services screen, but otherwise allowed.
• Send to LA Server. Enter the IP address of the computer or server on your LAN that will
receive the inbound traffic covered by this rule.
• WA Users. These settings determine which packets are covered by the rule, based on their
source (WAN) IP address. Select the option that you want:
– Any. All IP addresses are covered by this rule.
– Single address. Enter the required start address in the Start field.
– Address range. If this option is selected, you must enter the start and finish addresses in
the Start and Finish fields.
• Log. You can select whether the traffic will be logged. The choices are:
– ever. No log entries will be made for this service.
– Always. Any traffic for this service type will be logged.
– Match. Traffic of this type that matches the settings and action will be logged.
– ot match. Traffic of this type that does not match the settings and action will be logged.
Inbound Rule Example: Allowing Video conferencing
If you want to allow incoming video conferencing to be initiated from a restricted range of outside
IP addresses, such as from a branch office, you can create an inbound rule. In the example shown
in the following figure, CU-SeeMe connections are allowed only from a specified range of
external IP addresses. In this case, we have also specified logging of any incoming CU-SeeMe
requests that do not match the allowed settings.