7-4
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 7 Configuring AAA Rules for Network Access
Configuring Authentication for Network Access
Note If you use HTTP authentication, by default the username and password are sent from the client to the
ASA in clear text; in addition, the username and password are sent on to the destination web server as
well. See the “Enabling Secure Authentication of Web Clients” section on page 7-10 for information to
secure your credentials.
For FTP, a user has the option of entering the ASA username followed by an at sign (@) and then the
FTP username (name1@name2). For the password, the user enters the ASA password followed by an at
sign (@) and then the FTP password (password1@password2). For example, enter the following text:
name> name1@name2
password> password1@password2
This feature is useful when you have cascaded firewalls that require multiple logins. You can separate
several names and passwords by multiple at signs (@).
AAA Prompts and Identity Firewall
In an enterprise, some users log into the network by using other authentication mechanisms, such as
authenticating with a web portal (cut-through proxy). For example, users with a Mac and Linux client
might log into a web portal (cut-through proxy). Therefore, you must configure the identity firewall to
allow these types of authentication in connection with identity-based access policies.
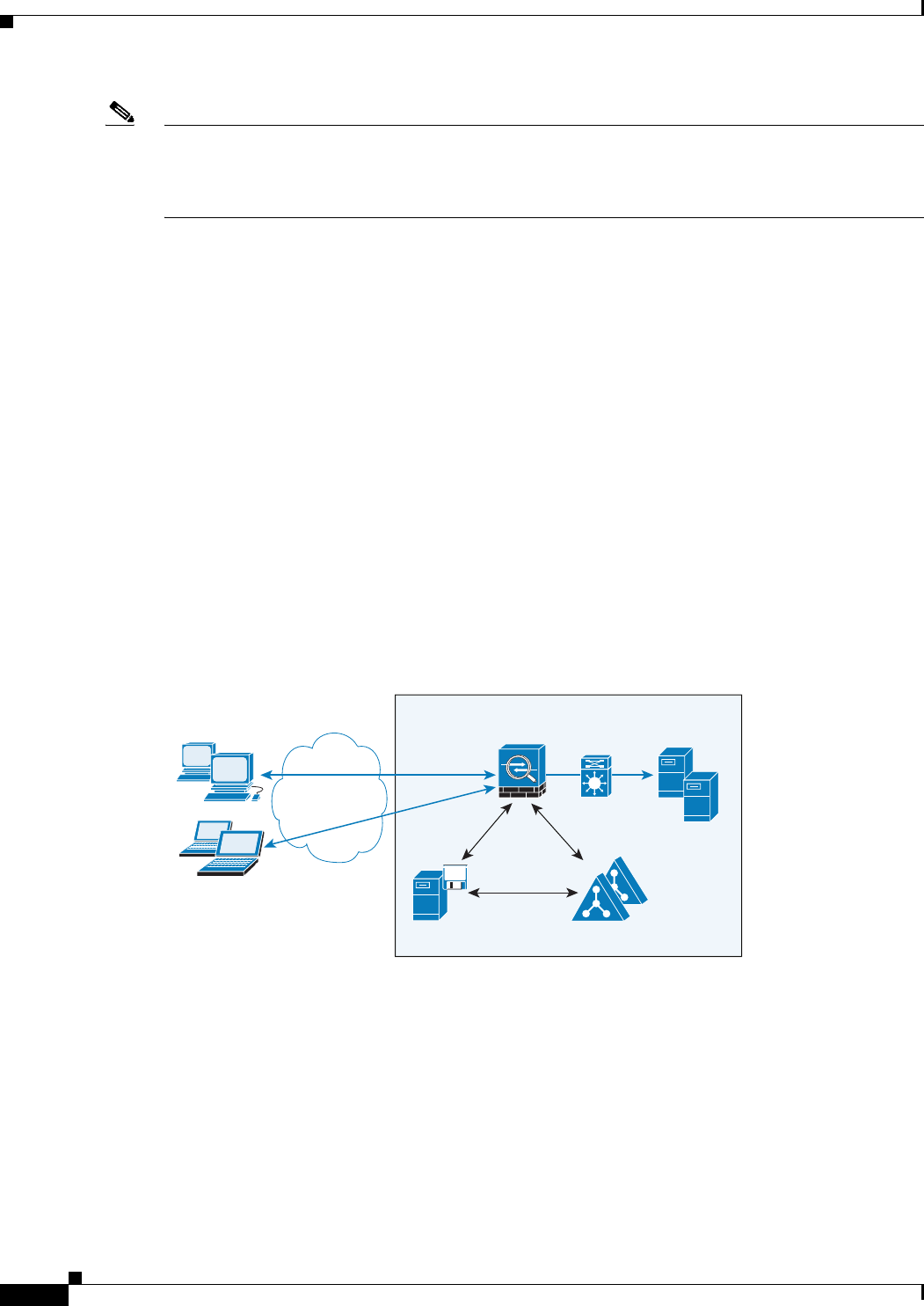
Figure 7-1 shows a deployment to support a cut-through proxy authentication captive portal. Active
Directory servers and the AD Agent are installed on the main site LAN. However, the identity firewall
is configured to support authentication of clients that are not part of the Active Directory domain.
Figure 7-1 Deployment Supporting Cut-through Proxy Authentication
The ASA designates users logging in through a web portal (cut-through proxy) as belonging to the
Active Directory domain with which they authenticated.
The ASA reports users logging in through a web portal (cut-through proxy) to the AD Agent, which
distributes the user information to all registered ASA devices. In this case, the identity firewall can
associate the users with their Active Directory domain. Specifically, the user identity-IP address
mappings of authenticated users are forwarded to all ASA contexts that contain the input interface where
packets are received and authenticated.
Users can log in by using HTTP/HTTPS, FTP, Telnet, or SSH. When users log in with these
authentication methods, the following guidelines apply:
• For HTTP/HTTPS traffic, an authentication window appears for unauthenticated users.
Inside Enterprise
334548
ASA
AD Servers
AD Agent
mktg.sample.com
10.1.1.2
WMI
LDAP
RADIUS
AD
Agent
WAN / LAN
HTTP/HTTPS
Windows Clients
(Domain Members)
Non-domain Member
Clients


















