17-7
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 17 Configuring the TLS Proxy for Encrypted Voice Inspection
Prerequisites for the TLS Proxy for Encrypted Voice Inspection
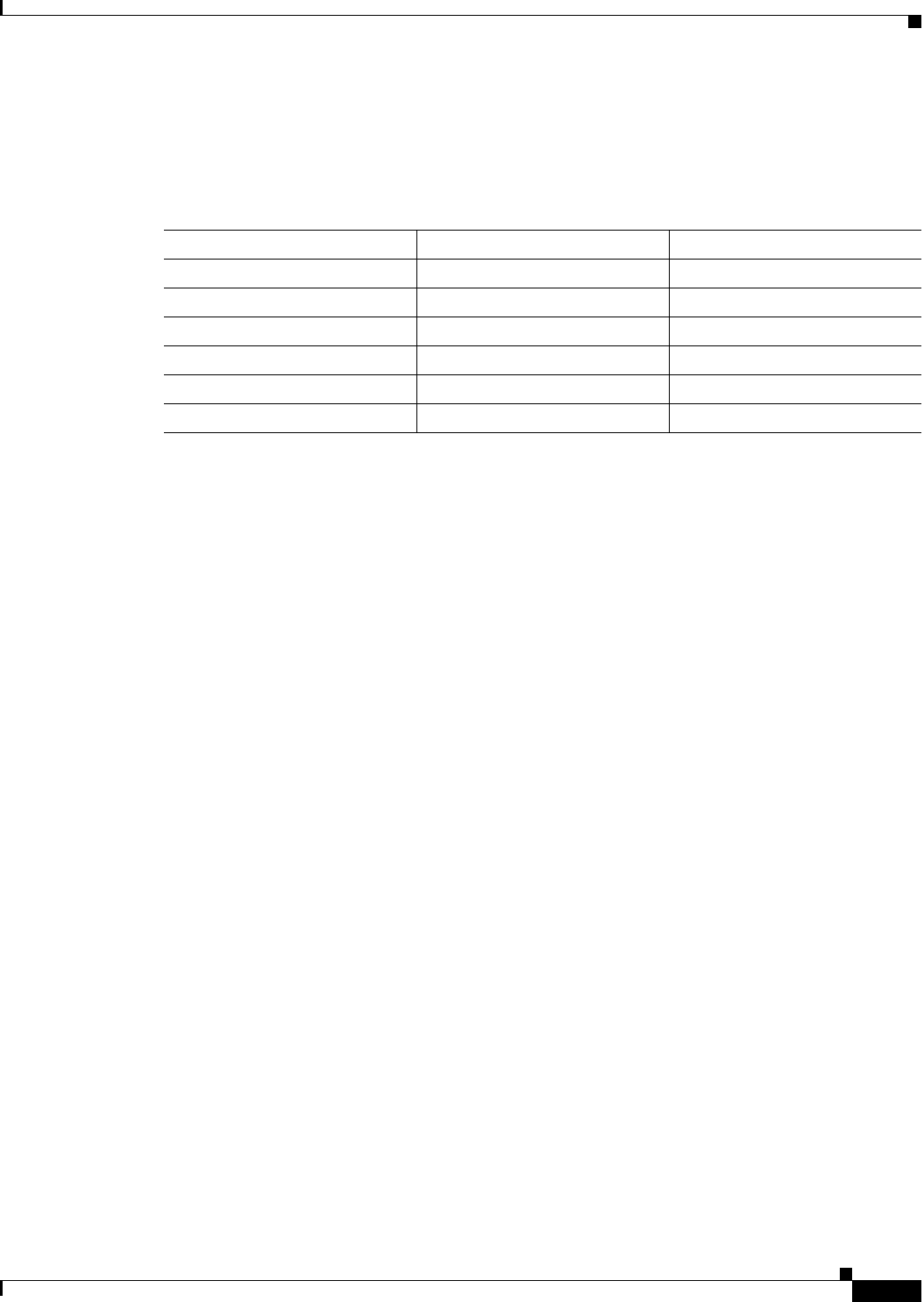
Table 17-1 shows the default and maximum TLS session details by platform.
For more information about licensing, see the general operations configuration guide.
Prerequisites for the TLS Proxy for Encrypted Voice Inspection
Before configuring TLS proxy, the following prerequisites are required:
• You must set clock on the security appliance before configuring TLS proxy. To set the clock
manually and display clock, use the clock set and show clock commands. We recommend that the
security appliance use the same NTP server as the Cisco Unified CallManager cluster. TLS
handshake may fail due to certificate validation failure if clock is out of sync between the security
appliance and the Cisco Unified CallManager server.
• 3DES-AES license is needed to interoperate with the Cisco Unified CallManager. AES is the default
cipher used by the Cisco Unified CallManager and Cisco IP Phone.
• Import the following certificates which are stored on the Cisco UCM. These certificates are required
by the ASA for the phone proxy.
–
Cisco_Manufacturing_CA
–
CAP-RTP-001
–
CAP-RTP-002
–
CAPF certificate (Optional)
If LSC provisioning is required or you have LSC enabled IP phones, you must import the CAPF
certificate from the Cisco UCM. If the Cisco UCM has more than one CAPF certificate, you
must import all of them to the ASA.
See Chapter 16, “Configuring the Cisco Phone Proxy.”For example, the CA Manufacturer certificate
is required by the phone proxy to validate the IP phone certificate.
Configuring the TLS Proxy for Encrypted Voice Inspection
This section includes the following topics:
• Task flow for Configuring the TLS Proxy for Encrypted Voice Inspection, page 17-8
2. With the 10,000-session UC license, the total combined sessions can be 10,000, but the maximum number of Phone Proxy sessions is 5000.
Table 17-1 Default and Maximum TLS Sessions on the Security Appliance
Security Appliance Platform Default TLS Sessions Maximum TLS Sessions
ASA 5505 10 80
ASA 5510 100 200
ASA 5520 300 1200
ASA 5540 1000 4500
ASA 5550 2000 4500
ASA 5580 4000 13,000