CHAPTER
19-1
Cisco ASA Series Firewall CLI Configuration Guide
19
Configuring Cisco Unified Presence
This chapter describes how to configure the adaptive security appliance for Cisco Unified Presence.
This chapter includes the following sections:
• Information About Cisco Unified Presence, page 19-1
• Licensing for Cisco Unified Presence, page 19-7
• Configuring Cisco Unified Presence Proxy for SIP Federation, page 19-8
• Monitoring Cisco Unified Presence, page 19-14
• Configuration Example for Cisco Unified Presence, page 19-14
• Feature History for Cisco Unified Presence, page 19-20
Information About Cisco Unified Presence
This section includes the following topics:
• Architecture for Cisco Unified Presence for SIP Federation Deployments, page 19-1
• Trust Relationship in the Presence Federation, page 19-4
• Security Certificate Exchange Between Cisco UP and the Security Appliance, page 19-5
• XMPP Federation Deployments, page 19-5
• Configuration Requirements for XMPP Federation, page 19-6
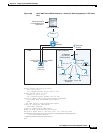
Architecture for Cisco Unified Presence for SIP Federation Deployments
Figure 19-1 depicts a Cisco Unified Presence/LCS Federation scenario with the ASA as the presence
federation proxy (implemented as a TLS proxy). The two entities with a TLS connection are the
“Routing Proxy” (a dedicated Cisco UP) in Enterprise X and the Microsoft Access Proxy in Enterprise
Y. However, the deployment is not limited to this scenario. Any Cisco UP or Cisco UP cluster could be
deployed on the left side of the ASA; the remote entity could be any server (an LCS, an OCS, or another
Cisco UP).
The following architecture is generic for two servers using SIP (or other ASA inspected protocols) with
a TLS connection.
Entity X: Cisco UP/Routing Proxy in Enterprise X
Entity Y: Microsoft Access Proxy/Edge server for LCS/OCS in Enterprise Y