3-2
Installation and Upgrade Guide for Cisco Unified MeetingPlace Web Conferencing Release 6.x
OL-13418-01
Chapter 3 Installing Web Conferencing for a Segmented Meeting Access Configuration
About Segmented Meeting Access
• About the SMA-2S Configuration and Video-Enabled Systems, page 3-4
About the SMA-2S Configuration
Note For requirements, refer to the “Segmented Meeting Access Requirements” sections of System
Requirements for Cisco Unified MeetingPlace at
http://www.cisco.com/en/us/products/sw/ps5664/ps5669/prod_installation_guides_list.html. New
installations of Cisco Unified MeetingPlace Web Conferencing Release 6.0 require a Cisco MCS.
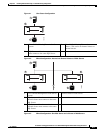
In the Segmented Meeting Access-2 Servers (SMA-2S) configuration, Cisco Unified MeetingPlace Web
Conferencing is deployed on two separate web servers or two separate clusters of web servers. One is on
the internal network, behind the firewall; the other is on another network segment, such as a DMZ. The
internal server or cluster is accessible only from behind the firewall, while the external server or cluster
is accessible from inside or outside the firewall.
While internal users have access to the full-access Web Conferencing user interface, external users have
access to an attend-only web page that allows attendance only to external meetings.
The SMA-2S configuration is the preferred and most secure deployment model if you want to provide
external access to Cisco Unified MeetingPlace web conferences.
We highly recommend that you configure external web servers to use Secure Sockets Layer (SSL). This
provides optimum security and resolves proxy server issues that can prevent users from joining a web
conference. (For more information, refer to the “Configuring External Access to Cisco Unified
MeetingPlace Web Conferencing” chapter of the Configuration Guide for Cisco Unified MeetingPlace
Web Conferencing at
http://www.cisco.com/en/US/products/sw/ps5664/ps5669/products_installation_and_configuration_gui
des_list.html.)
Note If you configure SSL on an external web server and users will access the server through a firewall, make
sure that TCP port 443 is open inbound on your firewall for both of the hostnames or IP addresses on the
server.