As previously mentioned, the file-sharing security model of the storage server is based on the NTFS
file-level security model. Share security seamlessly integrates with file security. In addition to discussing
share m anagement, this section discusses share security.
Share considerations
Planning the content, size, and distribution of shares on the storage server can improve performance,
manageability, and ease of use.
The content of shares should be carefully chosen to avoid two common pitfalls: either having too many
shares of a very spe cific nature, or of having very few shares of a generic nature. For example, shares for
general use a
re easier to set up in the beginning, but can cause problems later. Frequently, a better
approach is t
o create separate shares with a specific purpose or group of users in mind. However,
creating to
o many shares also has its drawbacks. For example, if it is sufficient to create a single share
foruserhom
e directories, create a “hom es” share rather than creating separate shares for each user.
By keeping t
he number of shares and other resources low, the performance of the storage server is
optimized
. For example, instead of sharing out each individual user’s home directory as its own share,
share out the top-level directory and let the users map personal drives to their own subdirectory.
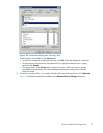
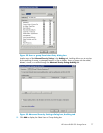
Defining Access Control Lists
TheAccessControlList(ACL)containstheinformationthatdictateswhichusersandgroupshaveaccess
to a share, as well as the type of access that is permitted. Each share on an NTFS file system has one
ACL with multiple associated user permissions. For example, an ACL can define that User1 has read
and write access to a share, User2 has read only access, and User3 has no access to the share. The
ACL also includes group access information that applies to every user in a configured group. ACLs are
also referred to as permissions.
Integra
ting local file system security into Windows domain environments
ACLs inc
lude properties specific to users and groups from a particular workgroup server or domain
enviro
nment. In a multidomain environment, user and group permissions from several domains can apply
to files
stored on the same device. Users and groups local to the storage server can be given access
permis
sions to shares managed by the device. The domain name of the storage server supplies the
conte
xt in which the user or group is understood. Permission configuration depends on the network and
domai
n infrastructure where the server resides.
File-sharing protocols (except NFS) supply a user and group context for all connections over the network.
(NFS supplies a machine-based context.) When new files are created by those users or machines, the
appropriate ACLs are applied.
Confi
guration tools provide the ability to share permissions out to clients. These shared permissions are
prop
agated into a file system ACL, and when new files are created over the network, the user creating the
file b
ecomes the file owner. In cases where a specific subdirectory of a share has different permissions
from the share itself, the NTFS permissions on the subdirectory apply instead. This method results in a
hierarchical security model where the network protocol permissions and the file permissions work together
to provide appropriate security for shares on the device.
NOT
E:
Sha
re permissions a nd file-level permissions are implemented separately. It is possible for files on a
file system to have different permissions from those a pplied to a share. When this situation occurs, the
file-level permissions override the share permissions.
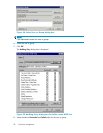
Comparing administrative (hidden) and standard shares
CIFS supports both administrative shares and standard shares.
• Administrative shares are shares with a last character of $. Administrative shares are not included
in the list of shares when a client browses for available shares on a CIFS server.
80
File server management