Intel® Packet Protect User’s Guide
12
Some enterprises may wish to create additional rules that govern communica-
tions between two specific computers.
Earlier, we introduced a scenario where the president and chief financial officer
of a company wished to implement extra security for their communications. For
this scenario, a new rule is needed. Let’s compare a possible rule for this sce-
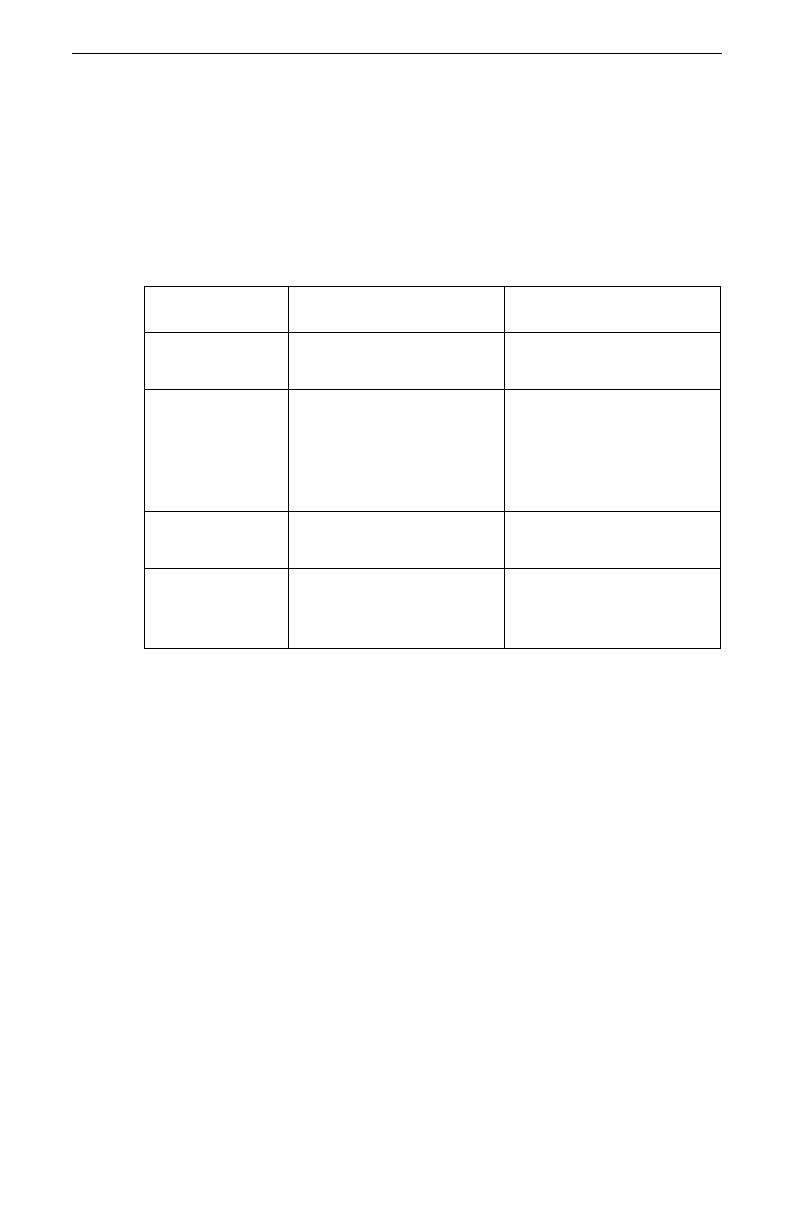
nario to the System Policy’s Default Rule:
In addition to these rules, both the president and the Chief Financial Officer
would have the Secure Initiator default behavior. The rule might also want to use
more secure options, such as perfect forward secrecy, which provides a very
secure negotiation of session keys. There are many other security options that
can be chosen when you create a security action for this rule. See “Customize
Security Actions” on page 33 for more information on options for security
actions.
By comparing the new rule and the default rule, you can see how the new rule
provides an extra measure of security. The new security action is much more
limited. Longer time and/or size limits on a security action can give an intruder
an opportunity to intercept and possibly corrupt packets. By denying communi-
cation in case of rule failure, you ensure that communication between these two
computers will never occur in the clear.
What are the Trade-offs?
A very important part of developing your deployment model is to consider not
only the initial deployment, but maintaining the System Policies on all the com-
puters that use Packet Protect in your network.
Clearly, the simplest model we discussed will be the easiest to deploy and main-
tain. When all computers use the same defaults—Default Rule, security action,
Table 1: Rule Comparison
Property New Rule Default Rule
Destination
Workgroup
President and CFO only Everybody
Security Action New Security Action: Up
to 15 minutes or 50 MB,
whichever occurs first.
Then, a new security
association is negotiated.
Default Security Action:
Up to 8 hours, then a new
security association is
negotiated.
Rule Failure Deny Communication. Allow communication in
the clear.
Authentication Use a new pre-shared
key, known only to these
two computers.
Use the System Policy’s
settings


















