Intel® Packet Protect User’s Guide
60
Packet Protect re-negotiates the IPSec settings only; it doesn’t need to re-verify
the identity of the computers because it is already known. This helps reduce net-
work traffic by reducing extra key generation.
If the security association is not renewed automatically and consequently
expires, a security association between the same computers will require both
IKE steps: pre-shared key verification and IPSec negotiation.
How IPSec Protects Packets
IPSec applies the selected algorithms to each packet that is protected by IPSec.
The algorithms provide one of the following protection features:
• Encryption and privacy
• Integrity
• Time and size limits
• Anti-replay protection
The following sections describe some technical detail about encryption and
integrity protection. The other features of IPSec are described in “Customize
Security Actions” on page 33.
Encryption
Use encryption to protect the confidentiality of packets. Encryption encodes
packets so they are unreadable unless the receiver has the proper key to decode
the packets.
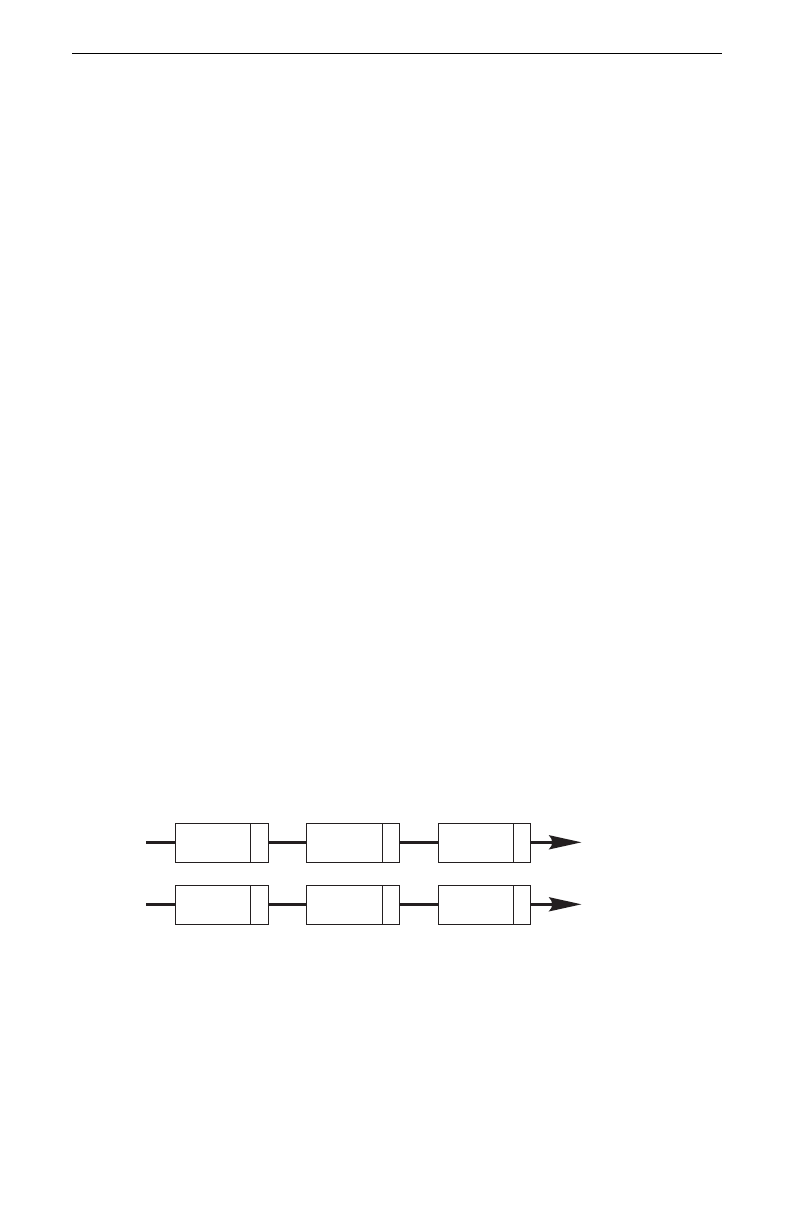
If a packet is encrypted using ESP encryption (DES or 3DES algorithms), it is
unreadable while in transit. Other types of encryption can protect the confidenti-
ality of information while stored on a computer – Packet Protect is designed to
protect the confidentiality of information while traveling on the network. The
following diagram shows unencrypted and encrypted packets traveling on the
network.
If the packets pass through any routers or switches, the encrypted packets are
relayed without requiring IPSec on those devices.
Integrity
Data integrity verifies that the packet was unchanged during transport over the
network. It also verifies that other packets where not inserted into the packet
flow. This helps prevent a computer from accepting packets from an intruder
who is attempting to send packets on the network.
pear apple banana
*&e# x2q%z k4!ht68
Packets “in the
clear”
Encrypted pack-
ets


















